I had the same problem, I reported it too and of course, I didn’t get any answer either… (although I have a paid license)
I also had this problem… I solved it
Same comments as everyone else here and the same observations…
To try and find out a little more… I installed Peerblock with many blocking lists (do the same and you’ll see) and found that the Comodo CIS firewall was no longer filtering, even though the Comodo CIS diagnostics said everything was fine.
IPv6 is blocked by my router.
Confidence in Comodo is falling month by month…
Then, have fun testing Comodo’s DNS, it doesn’t seem to be very efficient either…
Perhaps FlorinG is, once again, on his own when it comes to entering IP addresses…
I do not understand how you solved the problem… by solving the problem i took it as you were able to bring back comodo firewall to work again, right? Ahhh my bad I just noticed that solving comment was a reply to someone else… (fff so close… ![]() )
)
Asking me about sfc /scannow i took as offense sorry… i mentioned maybe not in this thread but in thread of previous version that i already did it… and i did it more than once… and dism and reinstalling windows with preserving apps and files… i wouldn’t post here a single post if i didn’t try any possible more or less aggressive fixing method with only one exception reinstall os from scratch (you’re talking to an it technician with 30+y combined personal and business experience).
Hello. Dear EricCryptid, if you remove Windows Socket Interface from the list of protected files in the HIPS settings to allow network connectivity for built-in applications. Then this action can weaken the protection of CIS, HIPS?
In fact, I simply disabled the firewall ![]()
![]()
Alas, it’s getting old and hasn’t been reprogrammed for too long.
It used to be my favorite firewall, but it’s getting old.
(with Agnitum Outpost in the old days ),
When my neighbor “mistakenly” connected to my Bluetooth, he didn’t see anything. I also had problems with the rights granted to Plesk.
Also, an application took out my documents to send them to the publisher’s site without my consent and authorized everything without seeing anything. Etc…Etc…
So I solved the problem as follows: I deactivated it.
Since then, I’ve been testing Glasswire and I’d also like to test MalwareBytes Binisoft WFC…
I’m waiting for Comodo to recover and be reprogrammed in full 64-bit by seasoned, well-paid programmers (no offshoring (too many coding errors, bugs and less trust)) to reactivate obsolete or buggy functions.
In the meantime, I’m paying the subscription, even though I think that if they really wanted to, the billions of dollars they have in their pockets would be redirected towards this, if that was their wish…
I am waiting for the fixes that were given to me by the COMODO developers with a list of more than 70 bugs to fix, this was last year in 2024.
To this day, the list of those bugs has not been fixed, according to the published changelog.
No, on the contrary, from what I hear right and left, there are others, but people just don’t have the strength to point them out anymore.
They don’t think it’s worth it anymore.
In fact, this forum is no longer even a forum for help between Comodo CIS users, because help can no longer be provided.
We’re stuck with bugs!
I’m starting to feel disillusioned…
Someone give me a link to download CIS version 12.3.3.8140…
You could already test this FW:
and later this one once the new version is released
Not overly. It was added to protect elevated privilege containment leak. You can tweak hips settings to fill that hole with that disabled but I’ve not experimented with it. See this post.
For info, you have to disable Core Isolation in Windows for Fort Firewall to work. The other option is to use a Windows Firewall front end like Malwarebytes Windows Firewall Control but neither have the capabilities to protect you like CF does as they’re just a Firewall and don’t have sandboxing, hips, cloud file analysis, default deny etc. I still think .8012 is the best stable but fingers crossed we’ll see some further development here.
I’m still using the 8012 and I’m happy with it, but it won’t last forever.
I’m not particularly optimistic about the future of CIS.
Given Comodo’s lack of professionalism and their lack of respect for users over the last few years, we need to look at alternative solutions.
I am aware of the limitations of Fort FW on core isolation (on my 2 laptops Microsoft refuses to activate it). Compared to other WFP-based FWs, I find it superior.
As for Portmaster, I’m waiting to see how stable the next version will be and what the acquisition of Safing by IVPN will bring.
I feel the same way as you.
We all know that antivirus is 0$ COST, but we don’t need to abandon ourselves and the product just like that.
We should have updates once a month or every 3 months, but we should have them.
I keep thinking that the more we talk about it, the longer it will be without a fix.
How to get back .8012?
Download from this topic: https://forums.comodo.com/t/comodo-internet-security-2020-v12-2-2-8012-released/320209
Hello, everyone!
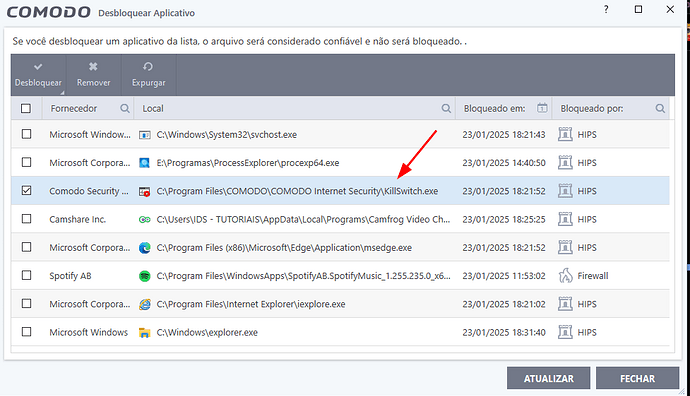
How can this happen?
The CIS itself with the HIPs module is doing this with KillSwitch.
Can anyone tell me why?
I’ve seen several bugs in CIS but this is going too far.
If anyone knows a way to solve this, please let me know.
Comodo HIPS blocks explorer, task manager and any programs trying to access Comodo files so they appear in that list even when blocked silently. Killswitch was probably trying to monitor the status of comodo processes so it was silently blocked from doing so. Killswitch will still work fine, it’s just comodo protecting itself. I wouldn’t stress over it unless there was a pop-up, it’s working as intended and protecting you.
I understand your explanation about Killswitch.
But there is another problem, if you look at the image it is blocking Edge and Internet Explorer, because I tried to use the virtual desktop, and I can’t connect to Edge.
Even though I unlocked all the security modules and Hips, the internet still doesn’t work inside the virtual desktop. ![]()