here is normal, but updates is very important help popularize product and company…
Hi Peace1,
Thank you for reporting.
Let me check this and update you.
Thanks
C.O.M.O.D.O RT
Hi Peace! Under NO circumstance should you take a file out of the VTRoot containment folder and just run it. Nest practice is to ignore the VTRoot folder entirely and just reset the sandbox daily.
Also, I am always curious as to why folk with Comodo will sandbox the browser. I can understand doing so with Sandboxie as there is no automatic containment of unknowns (which is a great deal more dangerous than those users realize), but not essentail at all with Comodo.
Hello Cruelsister and thank you for your response.
I understand that i shouldnt mess with the VTRoot folder but my question/concern still stand, if i can copy and paste files/folders from the VTRoot folder shouldnt Malware be able to do the “same” and run its payload outside the container?
Can you please elaborate on why sandboxing the browser is a bad idea?
Thank you
With Comodo it’s not that it is a bad idea, just not at all needed. Also I should have added that even if you pull a downloaded file out of Containment and run it, it will be treated as any other file- Comodo will either contain it if it is not trusted or allow it if it is.
But the one thing just as important as Containment is the Firewall. NEVER EVER ignore a FW alert. If the default action is Block, then do so. If you are in any way interested, this weekend I will actually do a Video on Youtube regarding Malware data stealers against Comodo Firewall- Look for “Comodo Firewall vs Malware Stealers” on the cruelsister1 channel.
Youre saying theyre other defence mechanisms in Comodo, yes im aware of that but if its that easy to copy and paste a file to anywhere outside the container then what is the purpose of the container regardless of other defense mechanisms? This is either a containment flaw or im ignorant on how Comodo containment works. Ill have a look at your channel, thank you.
the thing is: if a file is contained, than it will be on vtroot. if you run it it will be contained again… simple… the same for browsers: if you navigate into some dangerous site, if the site downloads some bad files, when it get runned comodo will block it. so no need to virtualize entire browser while with cis… but people get crazy with fear of the unknow and do a lot of crazy stuffs to protect their pc… the problem is that some changes will conflict with eachother and the computer will end up without any protection… so, installed comodo? let it be and just use your pc… atleast when its not bugged. if its running good, than let it be…
Hello Victor
I see, youre saying if i, for example copy and paste any file in VTRoot to anywhere outside the container and then try to run it, it will be contained again, same goes for any potential Malware? If this is the case then i apologize to ComodoRT, CruelSister and you Victor for wasting your time. Thanks for your responses though, appreciate it.
I confirm your explanation
Please let us know your demo once published. ![]()
Thanks
ZorKas
Peaxe1- Having a valid question is never a waste of time! My hope is that the explanations given above were clear.and of use.
there is no wasting time answering things that can help people. you are a user just like us, an interested user of comodo products, so, its the right way to go, helping each other.
if im wrond, cruelsister can corret me but doesnt matter whats going on, from outside, from inside, from within… if you have comodo firewall with containment enabled and configured nothing will pass, nothing will run without cis noticing you.
atleast it has being like that since i startetd using cis… and it has a long time…
im out cis right now as it is having some problems with my systems with win 10 22h2 and win 11 latest stable too. but as soon as comodo releases the new cis, ill jump back to it as i can trust it as a security monster ![]()
I certainly hope I’ll still be able to use comodo to enforce my VPN’s connection.
It’s idiot proofing for when I forgot that I disconnected it
Also, I don’t ever want certain applications to connect with no VPN, discord, and a few others that I use to communicate with people. I wouldn’t want certain unsavory types to figure out where I’m based…ever.
I realize CIS/CFW/CAV is still compatible and safe to use, but microsoft is constantly changing things for no good reason.
Comodo should be updated regularly so it stays compatible. God knows microsoft is never going to do it like they did it during the windows 7 days ever again.
For anyone who doesn’t know, in response to how bad vista was, microsoft tested every update for windows 7 on physical machines with every possible combination of hardware and software they could think of…which is why windows 7 ran so smoothly on pretty much every system it was installed on.
Now microsoft tests everything on VMs, so there’s very rarely any issues with software, but issues with hardware happen almost every time they make changes.
You can put that into Comodo “Kernel API Virtualization Mode” aka Containment/sandboxing…but not needed for the following reason…
Payload…the executable file is the problem…
Whether you use browser or anything else, these tools are merely “vehicles” for dropping a payload (eg: executable file)…
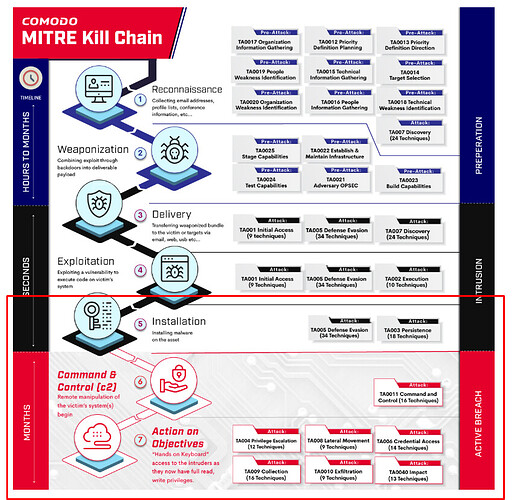
its steps 5 and after in the “Kill Chain”
Because Comodo monitors any and every request to execute an executable file, no matter where they come from and puts them into “API Virtualized Mode” it doesn’t really make any difference whether you run the browser (which is only a vehicle) in our “API Virtualized Mode”. Because if anything comes thru the browser (step 3: Delivery) as an executable file and its unknown to Comodo it will automatically virtualize it anyway!
I have marked in red box when Comodo kicks in, on the kill chain and virtualize…basically any unknowns will get virtualized automatically no matter what their delivery mechanism is.
Also: If you think thru “something has to copy and paste”…an executable file…where is that executable file running? Outside the containment? how did it make its way there? Just like the saying What happens in Las Vegas stays in Las Vegas

Same with Comodo… whatever runs in Comodo API Virtualization stays in Comodo API Virtualization ![]()
Indeed the sandboxing of a browser is pointless as the browser is never the primary initiator of a malicious process.
But while Comodo’s Containment is superb, the concurrent use of the Comodo firewall in blocking any outbound connections of contained nasties should never, ever be minimized or ignored.
That’s related to the uBlock rules post, how? Please tell you you meant to reply to someone else.
You are indeed correct. I should have explained further…
Once an Unknown executable file is Virtualized (so that it can’t cause damage, but still allowing you to use it, and thats the beauty of Comodo…) it is then sent to our Threat Labs in the Cloud to get a “Trusted Verdict”…
The reason why we say “Trusted Verdict” is because we put both Automated “AND” Human Experts to analyze these and not simply give a result of an automated system which is prone to both FP and FN (False Positive and False Negative).
We do NOT want to risk your security so we put Human Experts into our process therefore providing you a “Trusted Verdict”.
@Melih and my samples got detected by CAMAS/XAMAS as Malicious
I am using Comodo Firewall with custom mode
Many “clean” software installed on PCs send too much information about the user, which corresponds to “data heist”
Comodo once the rules are programmed in the firewall is a real safe
I confirm