hi @Avos-New-Forum , yes it will be fixed.
Thank you very much.
I await with confidence ![]()
Hello, CIS lovers,
Our next beta release plan has been finalized and we’ll share the new beta version on October 23rd, 2023.
Here is the list of bug-fixes that we’ll cover with the new beta version:
- Fixed an issue where icons in the taskbar disappeared after Explorer.exe restarted.
- Fixed the issue of missing the “Log as firewall event if this rule is fired” option on the firewall rule screen.
- Fixed issues with performing Quick Scan, Full Scan, and Rating Scan and errors related to updating the last scan date.
- Fixed the “Report a Bug” link being incorrect, outdated.
- Fixed an issue with the first beta version, which had compatibility issues with Win 11 x64 after installation and uninstallation, where the internet connection would be interrupted and a popup would appear in the CIS tray saying "The network firewall is not functioning properly”.
- Fixed an issue where clicking on the scan exclusion under advanced protection would crash the entire advanced settings window/menu.
- Fixed an issue where the antivirus still appeared to be running despite disabling all components in CIS and could not be disabled.
- Fixed the “TDT agent is not working” issue.
- Fixed the “Intel TDT driver not loaded” issue.
- Fixed the issue of displaying the IntelTDT options on the UI with not supported CPU. If the CPU does not support TDT, it will be written to the log, and then unload tdt.dll. Users will be able to manually delete TDT’s log files.
- Fixed an issue with CIS crashing after uninstalling the old version and installing the new beta version.
- Fixed an issue where firewall settings caused the internet connection is being cut after installation of CIS 2024 Beta.
- Fixed issues with cmd/diskpart or diskadminisration such as not being able to clean up all or create new volumes and formatted/deleted data/files restoring themselves after formation.
- Fixed translation errors in Russian, French, Polish, Italian and Portuguese.
Problems with Killswitch, Cleaning Essentials, recognizer, and updater will also be fixed.
Thank you for your patience, we look forward to seeing the results of your experience with the new beta.
Kind regards,
Comodo Team
I don’t know what to do with this, for example ![]()
C:\ProgramData\comodo\Cis\tempscrpt\C_powershell.exe_806C4F4A619CD1C9927A6A5F237CABF3BCB036F3.ps1
containing :
“Get-PhysicalDisk | Select BusType | ft -HideTableHeaders”
I don’t know who created it, when, or what it does.
Sometimes it’s understandable, others… not at all.
So, it’s very nice to warn about powershell tempscripts (or others?), but it would be even nicer if we knew where this is leading us…
Bravo to the whole team for this overhaul!
Hello kindly whether it is worth waiting for the new CIS 2024 Beta I am very happy with this information and thank you to the Comodo team for improving the Polish language errors with uncommonly waiting for Beta greetings from Poland.
Good morning,
There is a big problem regarding process control under CIS (beta).
Let me explain :
Since updating from Windows 10 to Windows 11 did not work with CIS, I disabled CIS from startup with Revo Uninstaller.
Failure.
Then, I completely uninstalled CIS with the Comodo utility and also with Revo for potential “leftovers”.
So, no more CIS at all.
So the update to Windows 11 worked.
Once on Windows 11 Pro (64), I wanted to reinstall CIS.
The installation went well, he didn’t notice anything or indicate anything.
But now, being used to the software, I noticed that things were not going right.
After several unsuccessful attempts at the diagnostics function, I tried several reinstallations. Without success either.
Then, I had the idea to look at the functions of controlling the users when starting Revo Uninstaller. The entries that I had blocked in Windows 10 to allow the system update were still blocked…
After checking them so that they are at the next startup, the installation worked and so did CIS.
I conclude the following:
- Any process can very easily prevent CIS from returning to the next boot
- CIS does not know how to realize that it will be blocked at the next boot
- CIS does not know how to reactivate at the next boot
- The installation of CIS does not notice the problem either and does not restore the start of the program to boot.
- But even worse… the diagnosis doesn’t know how to do it either…
- And don’t notice it either
It would still be super cool to correct this on this version.
With all the most sincere thanks in advance.
FYI, the CIS config was locked by a password.
I tried to do the same with another antivirus, sure enough, it came back perfect on reboot.
There is also the fact that Comodo CIS files should only belong to Comodo.
I was able to add Killswitch too easily (when it didn’t work on the first beta). The one I added is positive by 7 antiviruses on virustotal. I think I could have even added another exe and named it KillSwitch.
If we can so easily replace the official exe of the current version, this could open the way to out-of-control vulnerabilities.
It is just my humble opinion…
Otherwise… CIS cleanup tools does not uninstall Comdo Secure Shopping which remains in place after uninstalling CIS.
And Comodo SHopping works alone with its environment.

Sorry to keep coming back, but the beta testing period doesn’t last forever.
So I communicate everything I notice.
So… something else:
When you install the official version of CIS Pro, it starts doing an update as soon as the installation is complete, then a quick scan, then offers to restart the computer to complete the installation process.
With the beta version, I didn’t see an update starting automatically, nor an analysis, and not a reboot request each time.
However, I installed it several times…
Good morning,
A few messages above, I reported CIS malfunctions, particularly on the interface.
I was told that it was due to my configuration.
I’m a little disappointed…
According to you, from Spectrum, Oric, MSX, Atari, Windiows 3.1, 95, NT 4.0 to Windows 10 (and 11), how many software(s) have had their appearance broken by user configuration or by the presence of other software?
And how many times have I been told that in fact…it was my fault…?
I really don’t think this way of doing things is reassuring…
Since, in my opinion, I was not answered correctly, and if I were part of the software quality department, I would not let this pass, but also, because I really and honestly want CIS to really come out at its best of this beta, I cannot give up asking this question:
How is it that an external event (config, other software) can so easily intervene IN Comodo CIS and change its appearance?
I, in your place, would not let this pass.
A derailed appearance doesn’t make for the best publicity.
Hello again,
There is also something that would also be nice to correct in CIS Pro.
This is the license activation system.
On the same PC, sometimes it works, sometimes it doesn’t work.
And each time, you have to wait days for the “Subscriptions Service” to sort out the situation.
Why not use another way of doing things, as the competition can do?
I upgraded from Windows 10 to 11 to be able to test Comodo CIS: impossible to activate the license! (It worked flawlessly under Windows 10)
I am restoring my PC from a backup: unable to activate the license.
Sometimes I even change the config in CIS: it’s impossible to activate the license.
Why not take the digital fingerprint of the PC?
or see on online management that only one PC is connected to this license?
I have the right to three licenses, only one PC tries to take advantage of it, but it doesn’t work!
Please try to see, for example, what Adlice is doing with its licensing system for RogueKiller. It works perfectly!
If we have installed one license too many, we will manage it on the console, we delete the old PC and everything is in order again.
It takes 5 minutes!
I think you also rely on the IP address to validate the licenses, because once I was asked for it to reactivate my license
And then, there are many countries where Internet Providers do not give a fixed IP address.
This manual license validation technique dates from a time when VPNs did not exist. Furthermore, what should we do with the laptops of people who travel a lot and whose IP address is constantly changing?
The Comodo “subscriptions” team (in my opinion “the person”) should not be fired. She is to be promoted for having lasted so long with such boring work!
Likewise, after a System upgrade, the files being the same, except those brought by the system update, is it really worth letting CIS scan all the hard drives again for hours, while it already done it during license validation under Windows 10?
Why do you need to reactivate the license during a system upgrade?
Why not take the SHA256 fingerprint of the files to avoid a long and restrictive re-scan?
I really hope that with this new 2024 version, which looks very good and will be, you will have so many sales that it will be impossible to manage licenses by hand as you still do!
Best wishes and thank you in advance for thinking about it…
Where are the promised bug fixes of the bugs on the List of current bugs ?
Here I am, 12+ years later, hoping for a usable product, and yet this “beta” is nothing better than an “alpha”.
I REALLY want Comodo AV / Firewall to succeed, but until QC and UAT improve to an acceptable level, both the users and developers will remain very frustrated…
Hi Varan-de-C0m0d0,
Thank you for reporting.
We will check and report this to the team.
Thanks
C.O.M.O.D.O RT
Good morning,
Thanks C.O.M.O.D.O RT
News of the day:
-
CIS heats my SSD up to 90 degrees!
-
Before CIS, computer shutdown: 4 seconds
With CIS 10 minutes (What does he do during this time?) -
On Windows 10 and Windows 11, I thought it was functional (everything was green), but there was no indication that it was not. Why at the end of the installation and periodically during a quiet period for the PC, would CIS not do the check (Diagnostic) itself to ensure its status?
-
CIS creates a duplicate profile of the real browser profile.
For what ? -
For me, the quick scan is extremely fast, to the point that I seriously question whether it really works. Idea: It would be nice to bold the letters indicating that the analysis is complete
-
Idea: Why not use the same active circle graph (the same as the analyses) during updates?
-
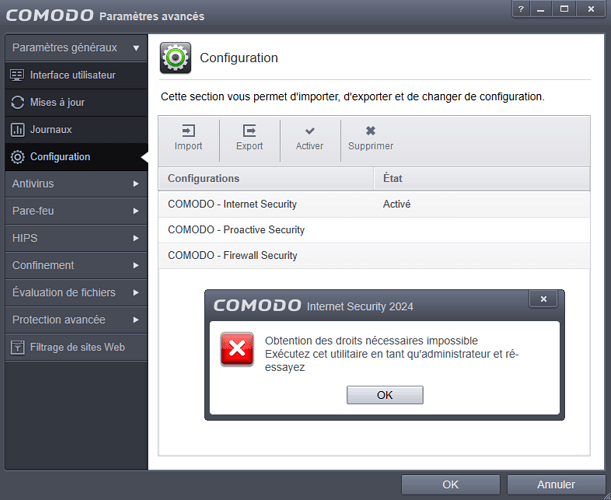
Impossible to save or load a config, access to the disk is refused (CIS is however alone on the PC)
Picture : Impossible to save or load a config, access to the disk is refused (CIS is however alone on the PC).
I noticed that this happened after restoring the system with a backup. At this point, the system disk is no longer encrypted by Bitlocker. I don’t know if there is a cause and effect link.
Still, with Bitlocker activated, no problem with CIS on this and with a restoration without Bitlocker, problems.
I also wondered if CIS was not partly (even very small) coded in 16 bits (the main part in 64 bits, a part in 32 and a whole part in 16 bits).
For what ?
I saw truncated file names, like in the past on much older Windows. This did not happen before installing CIS.
-
A quick pass under Ashampoo WinOptimizer allowed me to see that the uninstaller provided earlier on this page leaves some residue.
But also, after uninstalling, I sometimes have oem42.inf, eom107.inf, oem42.inf, oem.88.inf. Sometimes only two of them remain after uninstallation. So I think that the uninstallation utility must adapt to the Beta version… -
It looks like you have telemetry set up to see what’s happening with beta installs, correct?
Is private information circulating? I live in the European Union, the rights to private data are not the same. It is more restrictive. -
Without CIS my SSD lost 37 degrees… phew!
-
Are so few of us testing the beta version?
Note: My system is clean (Windows 11 Pro (64)
and SFC /SCANNOW does not find any errors
UAT = User Acceptance Test
QC = Quality Control
Helo Cavehomme !
I completely agree with you = it’s an Alpha release and I just wasted over two weeks trying to get it working for them.
In addition, I find myself on Windows 11 “because CIS had been even better adapted to Windows 11”, which is what I didn’t want! ![]()
![]()
![]()
![]()
![]()
![]()
I trusted, I regret. If they had openly said it was an Alpha that could crash the system, I would have installed it on a specific PC.
I was a little naive on this one… It’s not for lack of having participated in other betas from other publishers…
Hello Cisfan !
Comodo CIS is specifically second to none and that’s why we’re still here…
But…
But…
You have to write it down, CIS needs help with:
It’s time to fix all this with the new version.
Please !
You have to write it down, CIS needs help with:
- Silent mode firewall silently blocks network access for unrecognized applications and does not log the block.
- Firewall does not filter network access when windivert or wintun is being used. Cloudflare Warp which uses windivert, applications that use wintun are OpenVPN version 2.5 or later and Wireguard. Due note that Windows firewall and other 3rd party firewalls that use WFP can still perform application filtering when wintun and windivert are running.
- Sandbox bypass with ssts64 fileacc1.exe and filectl1.exe when run in containment, they are still able to modify files outside of sandbox. Fileacc1 is able to change the security descriptor of files/folders by setting deny to the “Everyone” user group. Filectl1 is able to overwrite file contents with NULL bytes using FSCTL_SET_ZERO_DATA I/O control code.
- HIPS/Sandbox bypass with SetVolumeMountPoint and DeleteVolumeMountPoint . The fix would be to hook the SetVolumeMountPoint and DeleteVolumeMountPoint WinAPI functions and treat it as a form of direct disk access like CIS does for the DefineDosDevice API function. That way you get a HIPS alert for direct disk access and it would be auto blocked when run in containment anytime an application calls these functions.
- No file source tracking for .msi files so auto-containment rules will not work for those .msi files.
- Embedded-code detection for misexec.exe does not work so msiexec.exe /I will not be detected.
- Excessive firewall logging of blocked events.
- CIS relies on device name paths instead of using normal file paths so it causes issues with scan exclusions and HIPS/firewall rules for applications/files located on removable media.
- Incorrect detection of direct disk access by non-contained applications that access files/folders that are defined in protected data folders. Only noticeable with unrecognized applications or setting HIPS to paranoid mode, topic about this issue.
- HTTPS filtering does not work with chrome browser or other chrome based browsers such as Microsoft Edge and Opera.
- Firefox and IE a blank page is shown instead of the Comodo block page when blocking/asking for HTTPS URLs.
- Other valid strings are still prevented from being used for web filter categories. e.g
https://*
13./.exe
14./img/ - Infinite loop of cloud scanner detection when executing an application that is detected by cloud scanner file lookup. Choosing clean or any of the ignore options will still bring up the alert and you can’t do anything else unless you hard shutdown the system.
- HIPS does not represent certain token privileges correctly, was fixed in 7092 but did not carry through to 8012.
- Can’t paste IPv4 address in global and application rules, it only works in network zones.
- Autorun analyzer and killswitch do not perform file rating lookup of files.
- AV still scans executable files even when the executable is listed under scan exclusions.
- Can no longer use pipe symbol | in protected files for blocking write access of contained applications running under one of the restriction levels. It gives an error message of please enter valid data.
- Network zone or firewall rules using a host name is unusable as the firewall will use all IP addresses in range from lowest resolved IP to highest resolved IP, instead of just the IP’s belonging to the domain. e.g. . So every IP address within that range will be blocked if you created a block rule based on host name type or used blocked network zones with host name type. However in the registry there is another value called Addrs that does contain a list of IP addresses that do pertain to the domain. But it seems it is not used yet? Topic link
- HIPS rules will get corrupted by being completely erased when a new rule is being created during system shutdown, such as when HIPS is in training mode or create rules for trusted applications is enabled in HIPS settings.
- HIPS rules using environment variables are not handled correctly as alerts will still be shown for applications that already have rules in place. One example is using paranoid mode and still getting alerts for svchost.exe and from explorer.exe to access keyboard despite rules already set to allow. Another example which is kind of related to bug 8. listed previously, using paranoid mode while executing applications on removable media or mounted volumes. When explorer HIPS file path rule is defined using the environmental variable %windir% (default HIPS rule), HIPS will always ask to execute the same application. Changing the HIPS rule path to C:\Windows does not alert again. Not limited to just HIPS rules as firewall application rules has the same issue, e.g. in both rule sections you can have a rule already defined for an application with the file path using the environment variable, and then another rule will be created for the same application when using create rules for safe applications or training mode. Also you can manually add an application rule with the file path of the environment variable while already a rule with the standard path exists. e.g. you can have both %windir%\explorer.exe and C:\Windows\explorer.exe defined as an application rule, you won’t get a warning indicating a rule for that application already exists.
- Contained applications can add/remove/change user accounts and groups, prior versions did not allow such action.
Sept. 9th Edit: This appears so far to only affect Windows 7, as during my PM discussions with COMODO RT, they could not replicate on Windows 10. - According to help documentation for the containment logs, it describes being able to see the process tree of the contained application but such feature does not exist, and the PID is also not being recorded in the logs.
- Microsoft Edge can not open any website or page when sandboxed. Topic link: Microsoft Edge can not open any website or page when sandboxed
- Sometimes the CIS tray notification icon does not render and leaves an empty space. Topic link: Comodo Firewall systray icon invisible [M2419]
- Windows security center does not always recognize CIS being active or enabled. Topic link: Windows security center does not always recognize CIS
- Over time an issue occurs where the cmddata file grows to an excessively large file size. Topic link: Large cmddata file
- CIS will constantly inform of a new update is available even when the latest version is installed, happens after updating to a new version using the internal program updater. Various posts reporting this issue scattered throughout, can’t be bothered to find all previous posts, but most recent topic here: Comodo version 12.2.2.2.8012 wants to install over and over and over again??
- Renaming a portset for which a firewall rule uses, it cause issues after re-naming the port set.
- HIPS ignores certain actions of applications that are running as the SYSTEM account. E.g. Direct disk, direct keyboard, direct monitor access. That means if an unrecognized application is elevated to SYSTEM, HIPS will not alert for various actions carried out by that unrecognized application.
- HIPS bypass on Windows 10 of proxytest.exe and wfpblock.exe from matousec’s security software testing suite 64-bit. Workaround is to add \RPC Control\LRPC to protected COM Interfaces.
- HIPS bypass/ignore of folder creation, so unrecognized applications will not generate an alert when creating folders/directories. Previous CIS versions used to monitor such action and HIPS alert references the action when an unrecognized application creates a new file, HIPS will say program is trying to create a new file/folder.
- HIPS does not monitor access to COM Interfaces that are of InProcServer32 server type, so even when adding a COM object interface by its ProgID or CLSID to protected COM Interfaces, HIPS will not alert on access to that COM object by an unknown application.
- Cannot run virtual desktop when Windows Defender real-time protection is active it will throw an error message saying “User data is corrupted, please reset Sandbox and try again”, this is the case when installing Comodo firewall only, workaround is to add the Comodo installation folder to Windows Defender scan exclusions. Topic link.
- The Anti-virus will not scan files larger than 40 MB even when the setting “Limit maximum file size to” in the scan profile is disabled. The AV should scan all files regardless of size unless the option is used to limit the maximum file size that the AV should scan.
- The scan option “Apply this action to suspicious autorun processes” for Anti-Virus scan profiles is not available when the theme is set to the arcadia or modern themes.
- VirusScope does not track file attribute changes that are performed by non-contained applications, so it cannot be reversed. But it does appear to detect file attribute changes for contained applications.
- Some VirusScope recognizers do not get detected for unknown applications that are running in containment but are detected when the application is not running in containment. E.G. Generic.Infector.4 will not be alerted for an unrecognized contained application that moves itself to startup folder, however if the same application were to do the same action without being contained, a VirusScope alert will appear to the user.
- Firewall blocks outgoing connection requests for trusted applications at system startup if they attempt network access before CIS UI is loaded(cis tray and alerts UI processes) causing many blocked events in the firewall log for those trusted rated applications.
- High CPU usage of cmdagent.exe process when a RAM drive is in use. Topic link .
- Green border around console applications when run in containment is no longer shown on Windows 10 21H2.
- Create rescue disk downloads older version instead of the more recent v2 version that can be downloaded through the standalone link.
CIS does interfere with updating Windows 11 when using an ISO image. Each time I update an Insider Canary build I have to uninstall CIS.
When you started using Revo you, the user, was allowing Revo to do what it does. This is not Comodo’s fault. This is the user tinkering with his system.
Comodo is the nanny of program behavior not the nanny of user behavior. The user can tinker his system to the brink of collapse where an unknown file cannot.
You are not understanding the above basic. I find this concerning for a long term user.
As to your comments about KillSwitch. Again this is the user tinkering with his system. If the instance of KillSwitch that you used was untouched (as shown by its signature) then the 7 detections at VirusTotal are false positives. The fact that you did not check this
Again you are not understanding that CIS is not nanny the user behavior; it is the nanny of program behavior.
As a long term user you should know this distinction and these types of posts make me question your contributions in general and possibly your motives.
I think I noticed that…
Most VPNs use their own network adapter and VPN adapters (or most) are not monitored, captured or filtered by the Comodo CIS firewall and some types of VPN adapters are not supported by Comodo so that VPN traffic always finds its way out (or its growth).
Is it possible ?
Will this be fixed?
Thank you for your reply Citizen_K,
Despite everything, I would have preferred a truly more technical answer, and not one that was almost legally oriented! I’m sorry that you obviously aren’t a computer scientist. But I hold it against you in no way.
Since you are blindly defending it, do you believe that the people who hang out on this forum are both there to destroy Comodo, or to help it?
However, I agree with you entirely: Comodo CIS is not made (for the moment) for users who only want to use their computer, as you say and demonstrate so well.
Because, as you say so well, in this case, it is too dangerous.
Based on your sound advice, I therefore note that its use is too risky for an average user, and therefore, I must look elsewhere if the grass is greener.
Unfortunately, I have the impression that you have not understood that this page is that of the beta version, you should think about giving your informed advice and your commercial recommendations on a more opportunistic page.
Your bias won’t help the beta.
“Everything is beautiful, everything is magnificent” never helps beta versions.
And neither does the technique of pushing dust under the carpet…
Behavior like this makes us the laughing stock of many on MalwareTips and elsewhere.
First you need to learn how to sweep your front door!
Note: RevoUninstaller does things very well and is renowned for it. Moreover, they are under control. And, no, it’s not normal that the brand’s own uninstaller doesn’t do things right.
P.S: My System works very very well without Comodo CIS, even more than perfectly well. Your intervention is therefore counterproductive, since it forced me to write this. I would still point out, for those who come here out of curiosity, that yes, you are not obliged to uninstall other security solutions when you upgrade Windows.
And as I sense in you an unconditional fan, I specify that not wanting to be a troll machine, I will refrain from coming to HELP for a little while.
I have already participated in other betas. The process of tracking bugs and beta tester comments always works better when it’s not public.
There are technical solutions for this (to report bugs) (and comments)
The CIS devs are super nice, hard workers, but it’s time to appoint them as leaders and give them a nice full team to finish the job.
They deserve it.