Good morning,
There is a big problem regarding process control under CIS (beta).
Let me explain :
Since updating from Windows 10 to Windows 11 did not work with CIS, I disabled CIS from startup with Revo Uninstaller.
Failure.
Then, I completely uninstalled CIS with the Comodo utility and also with Revo for potential “leftovers”.
So, no more CIS at all.
So the update to Windows 11 worked.
Once on Windows 11 Pro (64), I wanted to reinstall CIS.
The installation went well, he didn’t notice anything or indicate anything.
But now, being used to the software, I noticed that things were not going right.
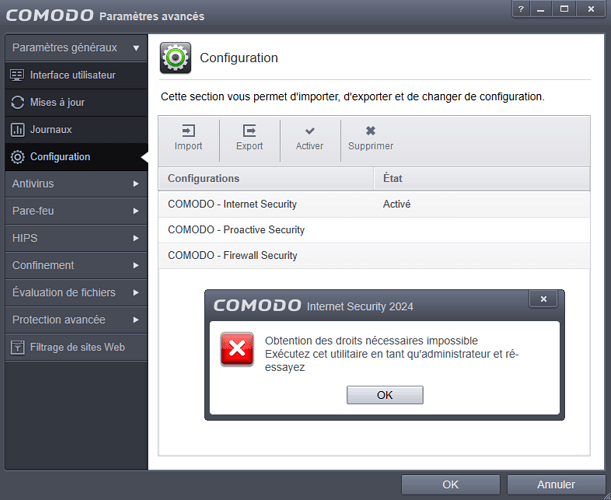
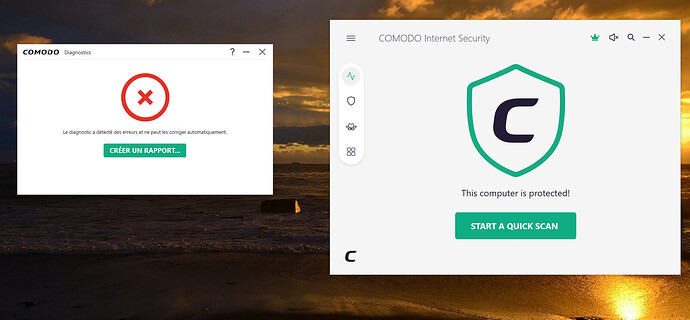
After several unsuccessful attempts at the diagnostics function, I tried several reinstallations. Without success either.
Then, I had the idea to look at the functions of controlling the users when starting Revo Uninstaller. The entries that I had blocked in Windows 10 to allow the system update were still blocked…
After checking them so that they are at the next startup, the installation worked and so did CIS.
I conclude the following:
- Any process can very easily prevent CIS from returning to the next boot
- CIS does not know how to realize that it will be blocked at the next boot
- CIS does not know how to reactivate at the next boot
- The installation of CIS does not notice the problem either and does not restore the start of the program to boot.
- But even worse… the diagnosis doesn’t know how to do it either…
- And don’t notice it either
It would still be super cool to correct this on this version.
With all the most sincere thanks in advance.
FYI, the CIS config was locked by a password.
I tried to do the same with another antivirus, sure enough, it came back perfect on reboot.
There is also the fact that Comodo CIS files should only belong to Comodo.
I was able to add Killswitch too easily (when it didn’t work on the first beta). The one I added is positive by 7 antiviruses on virustotal. I think I could have even added another exe and named it KillSwitch.
If we can so easily replace the official exe of the current version, this could open the way to out-of-control vulnerabilities.
It is just my humble opinion…