I scanned with other tools, nothing was found.
But I found it strange to say that it was dangerous, so I went along the path shown in the image I posted.
I exported the keys to the complete folder and threw it into the total virus.
NOTHING was found. But because CIS detected it, I was wondering why this was detected, could it be a bug?
That’s right, I took the entire folder with these keys and put it in the total virus to see if there was a threat, details were not found.
The question is why did the CIS detect it as a THREAT?
The question is why CIS did NOT recognize it as a threat in my case and why the firewall blocks dragon.exe (also in my case), but I still get a connection to the internet with dragon.
A good example of someone discovering a bug, a threat, but someone else not. An example of how a bug in one case is not necessarily a bug in another case (here: case = computer configurations).
In another forum, someone calls a software provider catastrophic because it has a download of only 200 kbps. My computer achieves over 35 Mbps with the same software - where is the problem to be found or who is responsible?
Any news about this?
(If an antivirus finds a threat in itself what do we do?)
If the team said it was a false positive I’d be OK.
Or perhaps you have a virus.
I’m currently waiting for a response on this. So far just waiting.
Because it’s at least strange for him to detect his own product.
Another quick thing from testing of this 2025 version:
when a malware is detected by the antivirus module and the “do not show notification - quarantine” is enabled, the malware is directly quarantined without any kind of notification. I’m pretty sure, in the previous versions, there was the notification of the detection, without prompting the user on the action to take, but at least the user was informed that Comodo has blocked something.
The answer is in this quote.
Yes, of course. But I remember that even with that option enabled, the antivirus was showing a baloon with the name of the identified threat and the location of the detection. The action was taken automatically (quarantine), like it should be, but at least there was the notification. Right now the user is not notified if something is happening in the pc and he/she would be just clueless of where the fresh downloaded file went. I’m pretty sure in CIS/CAV v10 was like I described.
Have you enabled “Show notification messages” in CIS settings? Make sure you allow CIS show notification in Windows Notification Settings.
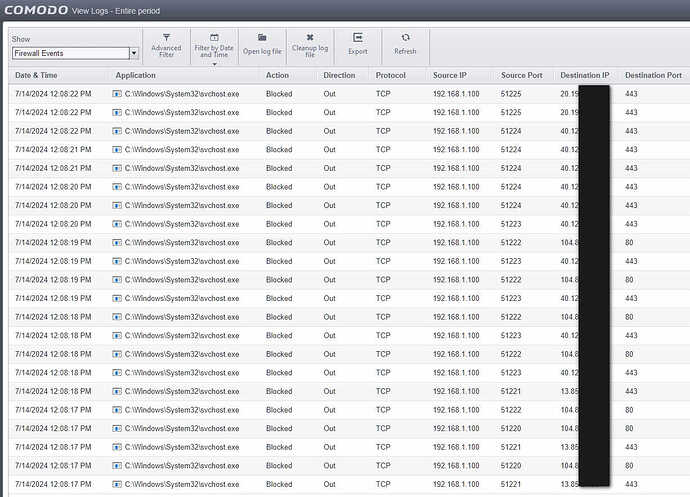
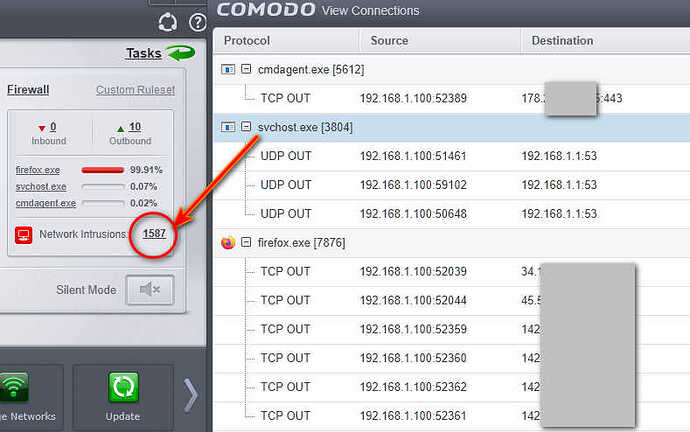
The C\Windows\system32\svchost.exe process saves the history of blocked IP address connections, even though I have the log disabled in the rule. Does anyone know where the reason is?
thank you in advance for your help.
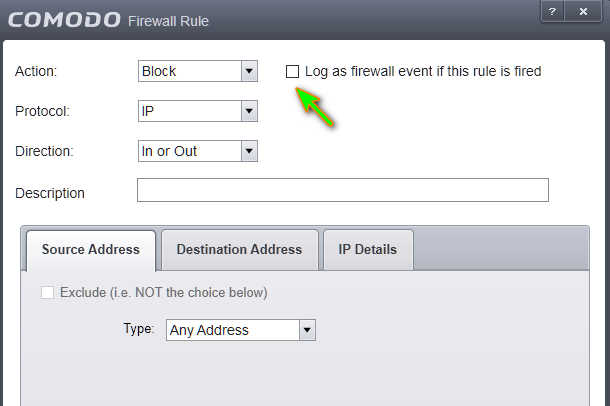
perhaps a suggestion: at the end of the global rules, would you have a broom rule that would log this event?
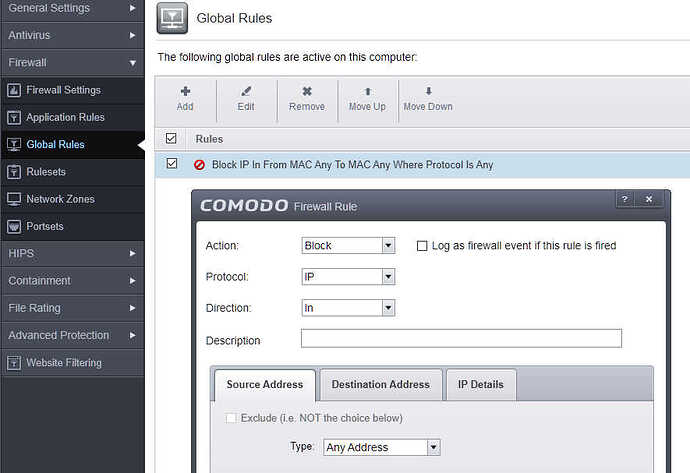
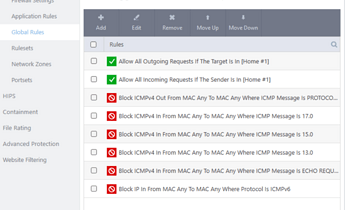
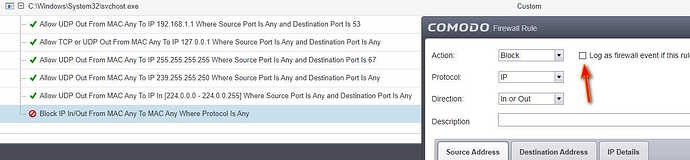
I don’t have history registration selected in the global rules, but thank you for the suggestion.
I have modified the global rules to block input because I have all the rules manually defined in the application rules
So I don’t even need global rules.
Please provide screenshot of logs.You will need to allow some connections with svchost, Particularly communication with the router but us seeing the logs may assist in resolving the issuse.
Hello and thank you for your response.
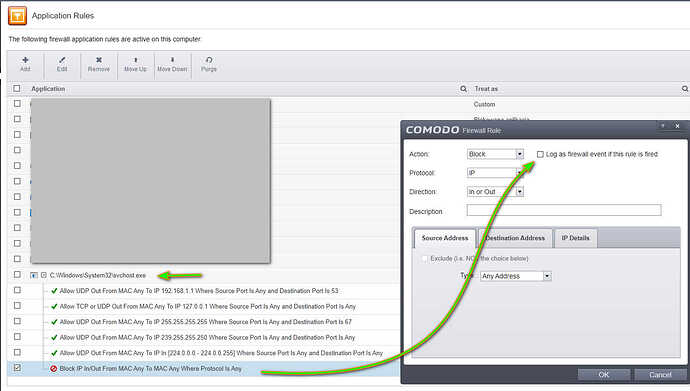
I have the minimum svchost.exe configuration rules and it works for basic WAN use. The WAN network works OK of course.
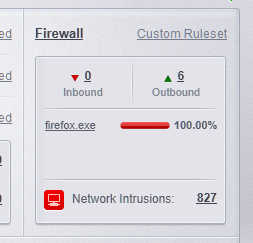
I don’t have log recording turned on anywhere, as you can see, the icons do not have a notebook, so registration should not take place. And yet, every second, a history of 4 blocked WAN IP addresses is written to the svchost.exe process.
Thanks for this information. Do the logs show all of the time or only for the first 5 or so minutes after startup?
Can you post a screenshot of your global rules?
Just trying to narrow down what the issue is.
The history is saved all the time from svchost and there are several thousand entries of IP WAN connections after a few hours.
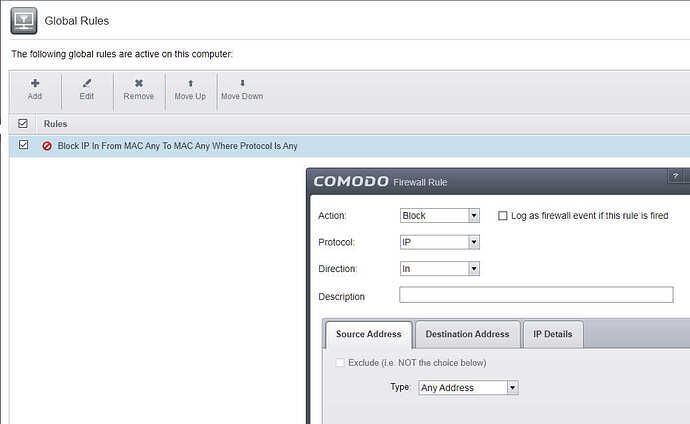
Global rules dump below
e.g… The number is already 800 blocks from only 20 minutes, where I previously deleted the log.
second edit:
number of svchost history entries after 35 minutes.
Looks like it’s just HTTP Requests for secure connections. You can always create a TCP Out to HTTP Portsets rule to get rid of the log spam but it may be triggering because of Global Rules or Network zones. What are your Global Rules?
Global Rules:
Creating restrictive rules for svchost isn’t needed really and can cause some problems. Any malware or unknown file that is a parent process of svchost, those svchost connections will be blocked, particularly if you are using the CruelSister setup.
Thank you for your reply.
Yes, I know what these connections are because I checked the IP locations.
As for the global rules, I showed earlier in the screenshot that there is only blocked input and no history logging. so I have only one global rule as in the screenshot.
Do you mean other settings here?
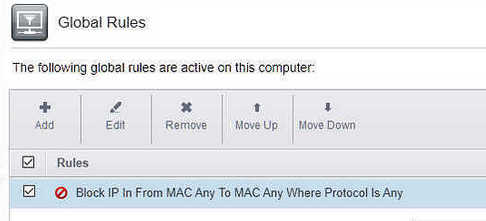
I have created all the rules manually in the application rules.
I know that tight svchost.exe rules can sometimes cause problems, but I have it under control and at least there is much less network traffic, which is mainly telemetry related.
This doesn’t change the fact that the log shouldn’t record history on svchost.exe if I don’t have the box checked, right?
If I have logging disabled, I don’t understand why CIS still saves logs in the history…
Are “all 8” global rules required?
Even if I don’t have them, it shouldn’t save log history for svchost.exe, …right?