Anyway, I applied them by hand, manually.
On the virtual desktop, I have access to all browsers and programs, except Comodo, which has consistently not functioned for many years in the virtual environment.
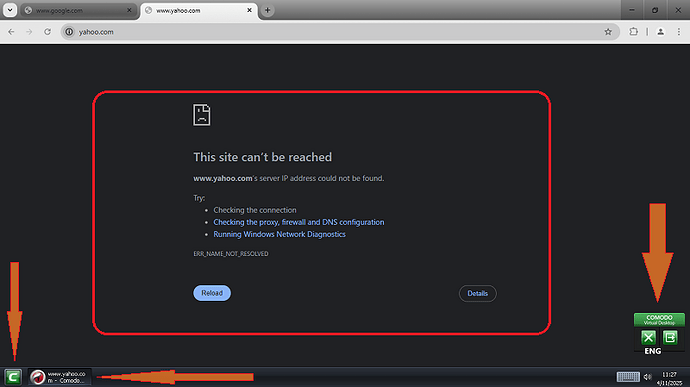
To me this seems like just a Fake AV browser advertisement. I don’t think any malware has been actually executed on that system
To fully analyze this issue we need at least a hint at the malware involved. If the infected computer still exists, what is being done at system start can be easily detected by simply looking at the Startup files via Task manager (can be done either in Safe Mode or startup with Command prompt).
This would at least give us an idea of what is occurring. Without any evidence of the actual malware involved further discussion is without any value.
Just one more clarification. You stated all of your files were missing. Was that just in the Virtual Desktop or your actual system? From memory, the Virtual Desktop environment gets reset when you Reset Container.
I agree with @cruelsister , we could do with seeing your startup entries or any log entries to be certain.
If your real OS is fine, it is also probable, as other suggested, that it was just a Fake AV page that floods your screen with popups.
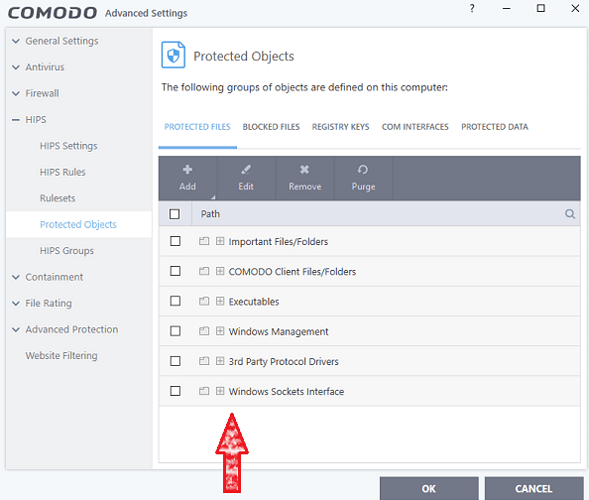
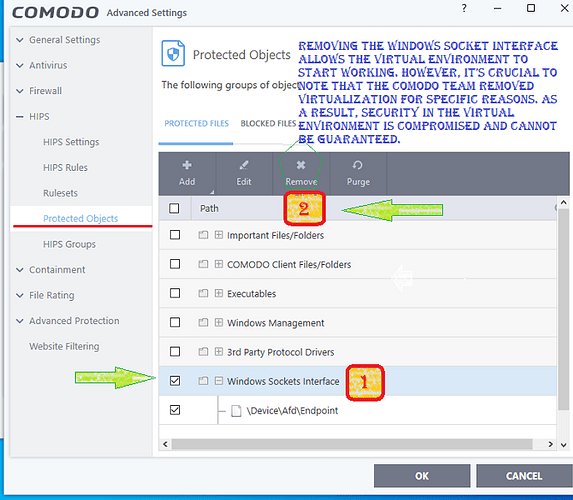
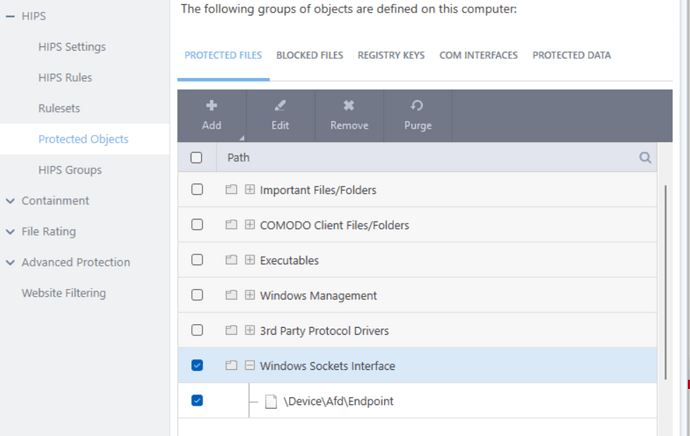
In the meantime, I know how to restore everything to its previous state by using the correct IP address, removing the Windows Sockets Interface, and booting from the Virtual Desktop. Please note that I do not store any confidential information on this computer.
Before proceeding, I will contact your specialists and provide them with full access to my computer to verify the presence of the virus. They won’t have to wait long, as I know where the open door is located.
After reinstalling Comodo Pro 2025, I encountered several issues:
1.The virtual desktop is not functioning and has stopped working due to existing problems.
2.Virtualization appears missing; I will attach video evidence of this.
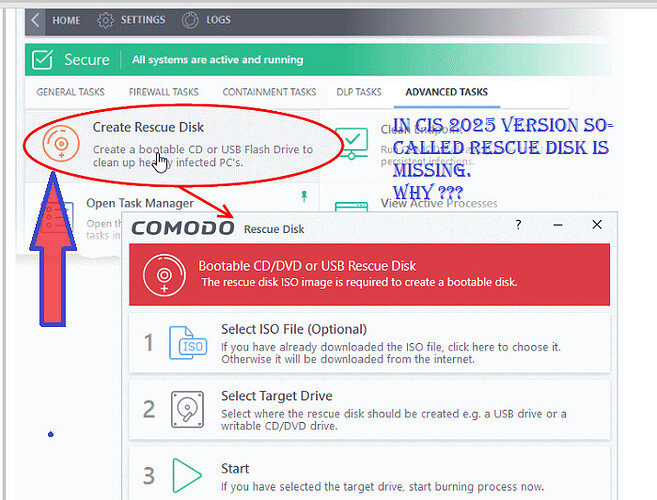
3.The rescue disk has been removed from the interface.
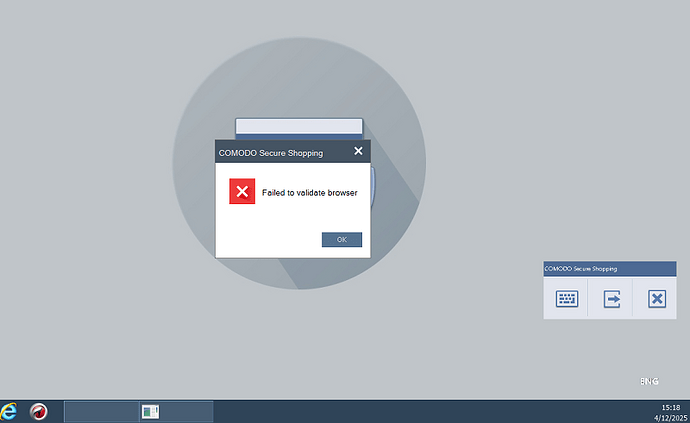
- Security shopping is no longer operational.
I experienced a hacking incident while working in a virtual environment. A bug spread throughout my computer, destroying all data.
I found information online indicating that many users have faced similar attacks related to Microsoft products. However, I was a target by highly skilled hackers using a sophisticated virus.
I have been visiting the published websites for the past ten years without issues.
It’s widely known that Windows has a relatively low level of security and virtually nonexistent privacy, especially in versions after Windows 7.
I use Linux on my computer and the second laptop and have never encountered any problems.
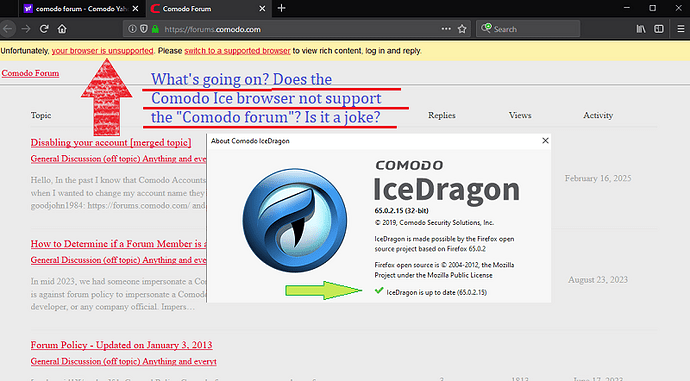
IceDragon is a Discontinued product and hasn’t been updated in a very long time, hence the forum message. ComodoDragon is updated regularly.
This is due to the elevated containment fix in the latest version. The Windows Sockets Interface in protected files was added and that broke connections with applications running in containment as described in this post.
Hi There!
I have provided specific information to government agencies in London and have been instructed not to disclose any details about this case, as it is currently under investigation.
I understand that some individuals among us are affiliated with Comodo.
If Comodo officials wish to contact the investigators, I can supply them with the agency’s phone number, the investigation number, and their email address.
Following the hack, I had an extensive phone conversation with special agents to answer all their questions regarding the hackers, including their phone numbers and methods of operation.
There have been individuals arrested. The investigating authorities have requested that I refrain from releasing any information while the investigation is ongoing.
Thank you for your valuable advice and practical guidance during our conversation.
P.S. I look forward to continuing our conversation once the investigation is complete.
I want to clarify that when I log in as either Stovan or London, both accounts are under my management. Thank you for your understanding.
You will get no joy from the NFIB if the malware arose in Bulgaria as they have no authority there and can only share such information with others.
Fraud in Bulgaria would only be dealt with internally (by Bulgaria itself) or more generally by the European Public Prosecutor’s Office (EPPO. These are were the NFIB would submit any information…
One day, I received three warnings on different days from Comodo that a computer was trying to access my computer and could tamper with it or take control of it. Comodo stopped immediately the Internet connections and terminated my virtual session.
I’m not an IT professional, but I figure cybercriminals could find a vulnerability somewhere that could allow a break-in or even tamper with the VDI by “taking over” the system, because 100% security can’t be guaranteed.
I’ve been working with Comodo for ages, and this was the first time I’d encountered something like this. No damage was done to my PC, nor was any data stolen, claims made, or any accounts (including bank accounts) accessed.
Hackers’ tools are constantly evolving.
Therefore, it’s certainly not easy to locate such a vulnerability. I’m sure I’m not the only one curious to see how things develop from here. Despite many doomsayers regarding security, I rely on Comodo based on my own experience. I even have my own configuration settings. That’s why experiences like this are so important.
I block all unnecessary remote access, even access from my computer dealer, who is certainly reliable and works for many well-known companies.
I researched the most common methods used by cybercriminals:
I appreciate your understanding that my knowledge of computer science and networks may not be as extensive as yours.
My challenges began with introducing a new router, which my grandson acquired from a seller on Alibaba or AliExpress.
NFIB’s investigation involves collaboration with Europol and Interpol, as the United Kingdom is a member of both organizations. This cooperation allows for effective tracking of fraudulent activities that may arise abroad.
I would like to remind you that during the first attack, I was working in a virtual environment. When a fake Microsoft message appeared on my screen, the entire keyboard and mouse were disabled. The only way to regain control was to turn off the computer.
During the second attack, the Control-Alt-Delete command worked, and I was able to open the Task Manager. However, I forgot to take the necessary screenshots.