So are you saying that when you restart your laptop the Virtual desktop is not open and that all the files you had there are gone? So it is doing what it should and reset the containment as it should ![]()
All the data disappeared from my laptop after rebooting.
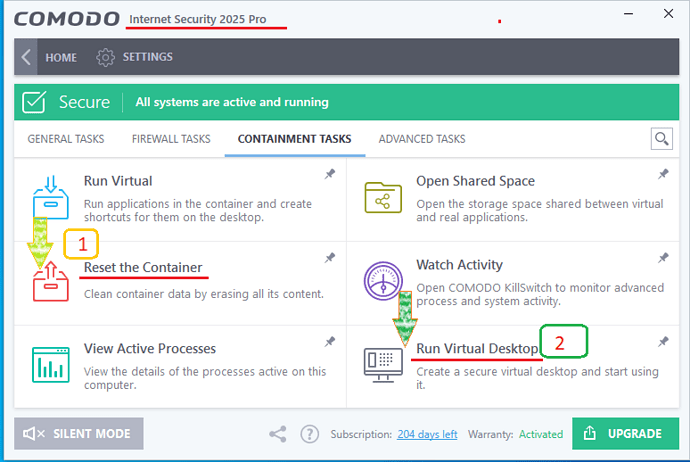
Here’s what happened, step by step: I turned the computer on and saw no indications of an attack. Since I prefer to work in a virtual environment, I reset the container and run a virtual desktop.
However, a short video report indicated I had been hacked within the Comodo Virtual Desktop. While finishing my coffee and contemplating my next steps, strange pictures suddenly appeared on the screen, accompanied by a continuous, disturbing sound.
I attempted to exit the virtual environment (virtual desktop), but the keyboard and mouse were unresponsive. Fortunately, the “Control-Alt-Delete” option worked, and I could exit the hacked account.
I have four accounts: one administrative account and three others. I opened the second account, but within 30 seconds, the same pictures and sounds reappeared. I closed that account using “Control-Alt-Delete” and then logged in to the admin account to delete both compromised accounts.
However, in less than 10 minutes, the same issue occurred with my admin account, forcing me to turn off the computer. A warning had appeared, advising me NOT TO TURN OFF MY COMPUTER.
When I restarted, I was shocked to discover that all my data was gone. This included everything: Comodo Internet Security 2025 Pro, the Comodo IceDragon browser, Comodo Dragon, CCleaner, Spybot Anti Beacon, my documents, pictures, videos, and more.
I then used the COMODO Rescue Disk to clean the laptop and restart Windows 10 Pro. After the system uploaded, I accessed Clean Endpoint. After about 35-40 minutes, Comodo detected a virus on one drive. When I chose to delete it, everything on the screen disappeared. Someone destroyed all the data, forcing me to start from scratch.
Well, life is stranger than fiction sometimes. ![]()
Greetings London, all this is interesting, strange and suspicious. The COMODO team needs to figure this out.
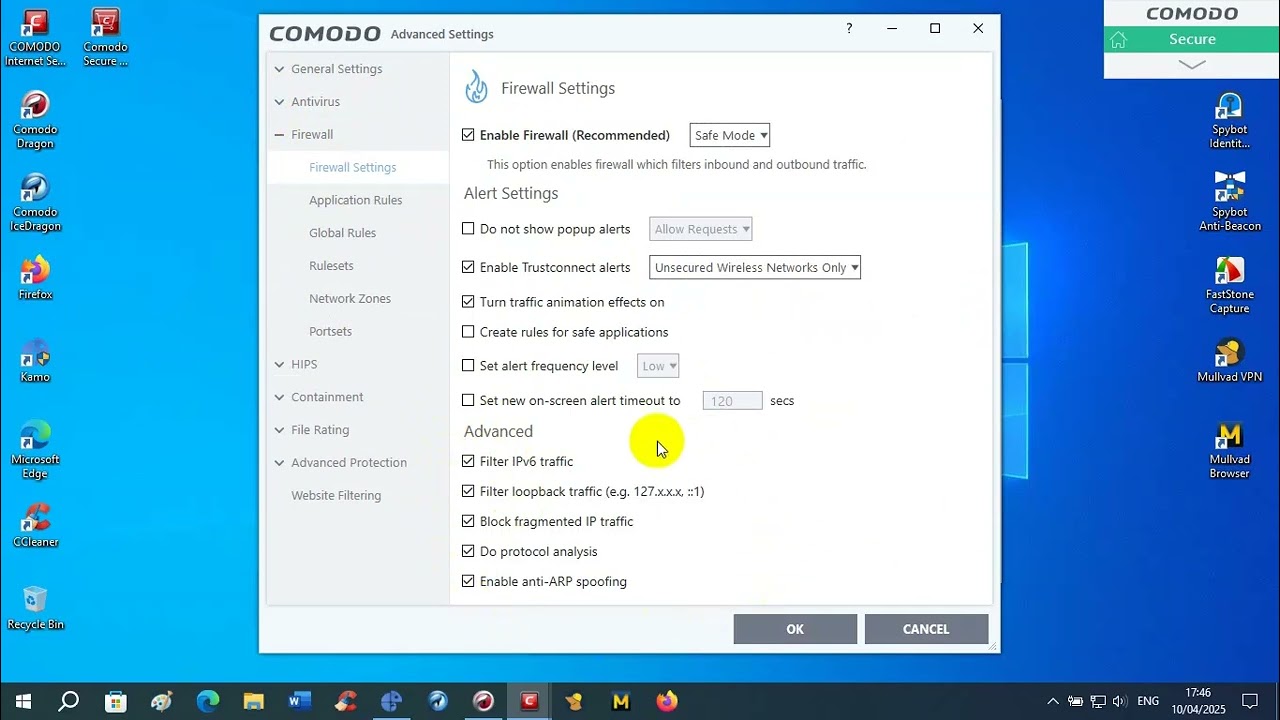
So, are you saying the infection has jumped across from the Virtual desktop to infect all your accounts on the machine - which is concerning - or are you saying the infection occurred on the machine and COMODO did not give any warning as to a suspicious file or no popups at all ? In your second post it states that you have Proactive Security as active, but have you made any other changes apart from those in the 3rd screen shot where you have all the Advanced boxes ticked ?
I agree with you. I have always trusted Comodo and am confident that we will handle these scoundrels effectively.
I am ready to cooperate in resolving this case. You have an incredibly talented staff, but I suspect that an insider may be involved.
We can discuss this further a little later, as it is currently five o’clock in the afternoon in London, and I am quite busy.
``Your Statement.
“,… are you saying the infection has jumped across from the Virtual desktop to infect all your accounts on the machine - which is concerning - or are you saying the infection occurred on the machine and COMODO did not give any warning as to a suspicious file or no popups at all.”
--------------------------------------------
BothI am also waiting for a position from COMODO, since it was clear from our friend’s explanation that the containment was bypassed.
Really interesting. I’m still trying to identify how this is possible. I do see the icon on your task bar but that’s just a program link it’s not showing on the right hand side. Can you click the ^ and show that CIS/CF is running?
CIS has built-in self protection and cannot be terminated though there was an elevated cmd line issue that disabled one of CIS’s services but that was after reboot and you’d have an x on the CIS icon. What changes did you make to the Proactive configuration?
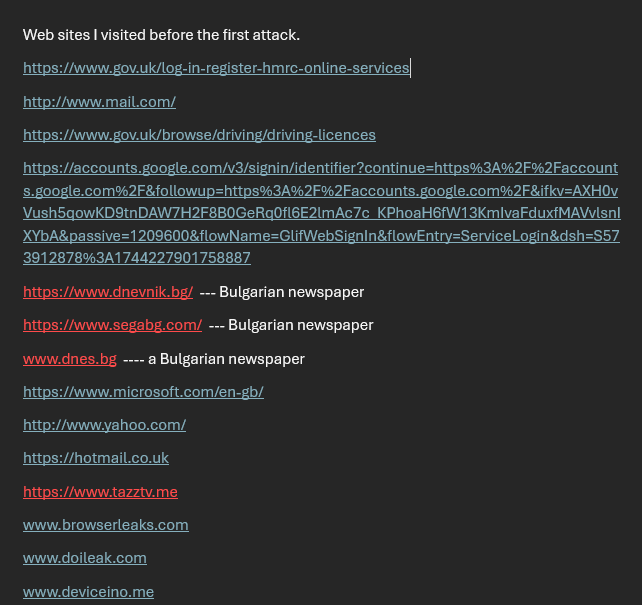
What website were you viewing when the issue occurred?
Will be interesting to see if @cruelsister has seen a similar attack or whether it’s even possible.
A good thing to have been done is to isolate the malware, which seems to have been loaded up on system start. This could have been done by booting into Safe Mode and looking into Startup (via task manager). From here one could determine where the malware resides.
This is important as with the original malware it could be shared to the community for analysis and replication (if you would chose to share).
It would be perfect to share this Malware, for the team to analyze, so that COMODO can block it. ![]()
Greetings EricCryptid. Maybe the leak really happened via (virtual desktop). Didn’t you say that this feature is outdated and unsupported, which means it doesn’t work well?
Secure shopping has not been updated, is no longer supported, and was removed from the latest major CIS release (so it may not work properly with the latest CIS or with Windows 11). Whereas Virtual desktop was updated, is part of the latest CIS, and as far as I know, it is working properly (with the caveat that you may need to tweak CIS to allow web browsing in the Virtual desktop).
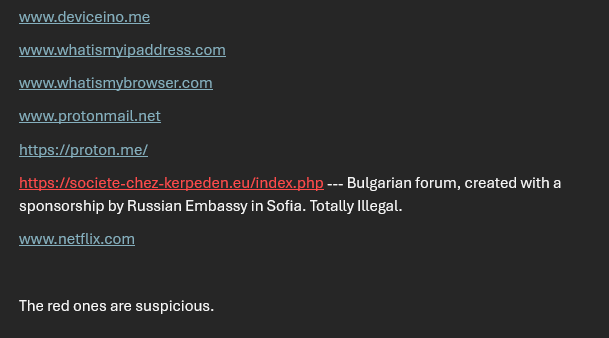
Sites marked in red are considered suspicious because they host forums where administrators employ programs that allow them to monitor participants through the cameras on their phones or laptops.
In the summer of 2019, I had a personal conversation with one of the administrators from a closed forum of the SEGA newspaper. They knew when I was smoking a cigarette or drinking coffee while I was working in front of my laptop. They could even identify that my conversation partner had an American accent, despite the fact that I had turned off both the microphone and camera on Windows 10 Pro.
The administrator used a hacking program that left no traces on the network. This program could monitor any participant and listen to conversations happening near their laptops or personal computers. At that time, I also had COMODO Internet Security, but the protection program did not alert me at all, and no internet security software could detect those who were monitoring through the camera unless it was physically covered.
Only the military operating system TENS was able to thwart such intrusions. Eventually, the hackers were exposed, and a large sum was paid out, leading to the closure of the newspaper’s forum.
I have never seen anything like this in Hollywood movies, but it seems that Sci-Fi productions have a lot to learn from real-life events.
I have this operating system because I served as a high-ranking officer in the army, and I also possess the necessary chip card. ![]()
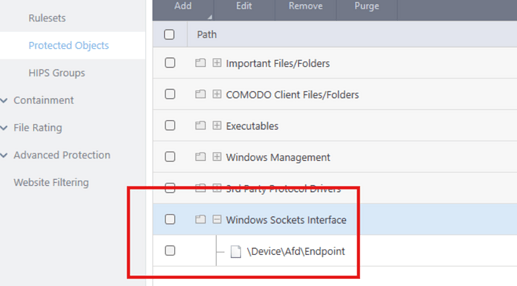
Thanks for the video. You didn’t show your HIPS Protected Objects or Containment settings. Out of curiosity, does your Protected Objects include the below?
Anyway, thank you for the detailed information. Looks like something happened on one of those dodgy websites.
I will also make another video report on what happens inside the Comodo Virtual Environment, considering I use the latest version, 2025 Pro.