I’m pretty sure you’re wrong. Just logging off and back on doesn’t re-initialize non-user level componentry. I always reboot (as oposed to logoff/logon) when leaktesting. This way I KNOW the PC is in a known state.
Ewen ![]()
I’m pretty sure you’re wrong. Just logging off and back on doesn’t re-initialize non-user level componentry. I always reboot (as oposed to logoff/logon) when leaktesting. This way I KNOW the PC is in a known state.
Ewen ![]()
Explorer.exe stopped responding in my PC… :-[
After I click on the test (the test 1) button, explorer crashes and… nothing happens. My firewall doesn’t show any message. However the text I typed is not shown too.
Do u think is my f/w bad or what?
And, because nothing happens, I doubt whether my f/w is still protecting me or damaged by the leak test (:NRD). Is this possible? ???
(R)
comofrog,
This explorer.exe crash sometimes happens on potent leaktests. It’s not permanent, nor does it do any damage. Simply reboot and you’re fine again.
Sometimes leaktests will even crash the user-end of the firewall - the GUI, where we interact with it. This means the systray icon will disappear; might even get a message that the firewall has crashed.
With CFP, this does not mean that the firewall is no longer working. There are two processes for CFP… cfp.exe (this is the gui; the systray icon), and cmdagent.exe (this is the core of the firewall).
If you are ever concerned about the firewall be in operation, open Task Manager and look for those two processes; the most important one is cmdagent.exe.
LM
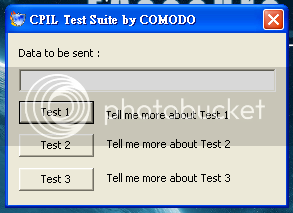
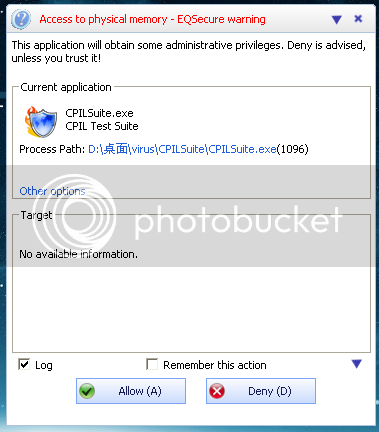
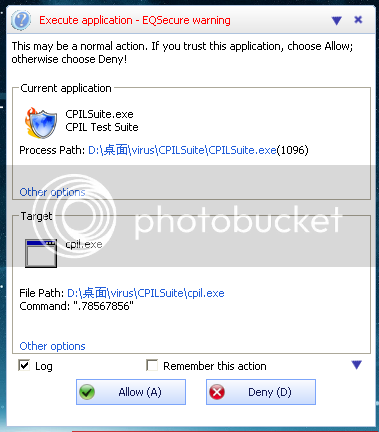
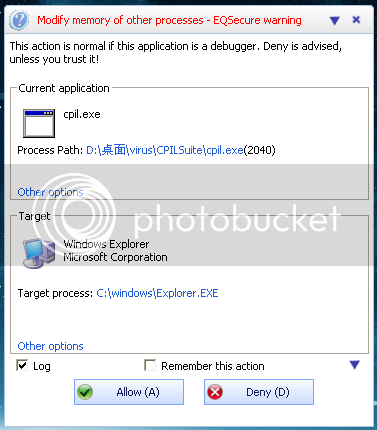
I tested the EQSecure first !
Test 1
Deny
Allow
Allow
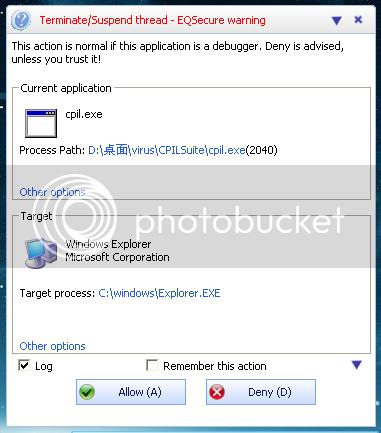
Allow
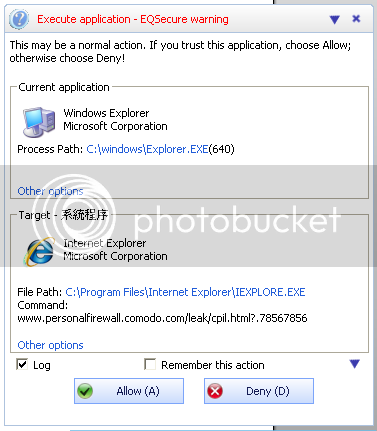
Deny
Test 2
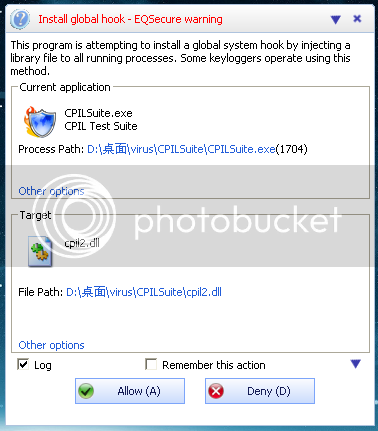
Deny
Test 3
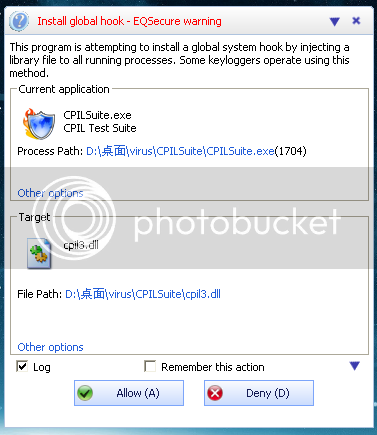
Deny
Then, I tested the CFP V3.0.8.214
Test 1
Test 2
block
Test 3
block
I have one XP computer with Comodo firewall, and a computer that I am repairing that now has Comodo–both passed. I have one Vista with TrendMicro–it failed on test 2.
Hello,
This type of testing, I find amusing. This for me is like an anti-virus program vendor creating and re-leasing a virus,… then stating,… “we can protect from this”
As I have posted concerning such simplistic as ARP protection,… protect from these known issues rather than creating your own possible problems, than protecting from these.
I, for one (possibly) am more concerned from attack from outside my PC.
Protect fully from outbound attack first.
Regards,
Vulnerability research is a big area, as you know Stem.
Do you rather we don’t explore vulnerabilities and when finding them don’t protect our users and brush it under the carpet?
BTW: its much easier to create viruses than finding vulnerabilities, so comparison is an unfair one. Finding vulnerabilities require indepth knowledge of the system, whereas anyone with a computer can create virus by simply downloading virii kits without even knowing how to program.
Melih
The first time I tried the test I did not reboot between attempts. It passed 1 and 3 but failed on 2 (firefox is my default browser). I rebooted and tried 2 alone and it passed then. My question then is, Doesn’t this mean a two prong attack could get around the firewall? If malicious software tries something along thing along the lines of test 1 as a feint. Then, after it is denied, immediately attempts something like test 2i It would go through without a problem. Seems like a problem to me! (:SAD)
Either way I tried this with ZoneAlarm and it failed all three. So it’s still a huge step in the right direction! :■■■■
The thing with any “test” application is that it’s a “proof of concept.” In other words, it is designed to show you how the software responds to a certain specific scenario. It’s there to help the user understand the software, and isn’t really (IMO) a solid indicator of all aspects of its security. In other words, what the test does isn’t specifically/exactly what malware does. For one thing, you KNOW you installed CPIL. You KNOW you ran it. You’re KNOW you’re going to get a popup.
When it comes to malware, you will typically see some filename that you’ve never seen before, and know nothing about, like 23o84swdfrki.exe (frequently in a “temp” file). Thus, it’s easy to realize that you need to deny. Do I advise you to reboot between malware infections? I hope you’d do more than just that… But I also hope you’re not just infecting your computer to see how it responds, either! ;D
LM
I’m using the latest and greatest CPF 3 (downloaded and installed clean today) and I failed tests 1 and 2, even after hitting “block” for the firewall test 2. Test 1 gave me no popup, it just went straight through.
Should I be worried?
errr, i’m not sure but i fail all of the tests.
i chose allow when DEFENSE+ alert show up (CPILSuite.exe is trying to install global hook…). did i do it wrong? what if i only install the BASIC FIREWALL ??? i can’t pass the test? same goes with other leaktest apps from www.firewallleaktester.com.
defense+ was detecting the dangerous behavior right?it’s got nothing to do with allowing/blocking something from/to internet, am i right? why the Firewall itself didn’t do anything when CPIL try to connect to internet?
and i’m sure i didn’t tick “remember” when i was allowing CPIL, but the second time i try the test, no alert at all ???
Hi ganda
What do you have the Security Level of Defense+ set to?
hi Kail (:WAV)
defense+ = train with safe mode.
hey try this (attached).
i think i get it now (maybe). when i execute the leaktest app, d+ warns me about explorer.exe is trying to execute PCflank ==> i allow it (in reality, we’ll not authorize something we don’t know that easily).
then d+ warns me about PCflank try to do something about Service control manager, and if we allow it, the result is : failed.
so maybe, IF we grant permission for something to take over an allowed/trusted app, we basically give it a ride to do anything.
so defense+ is an inseparatable component in V3, (not like V2 with lots of pops up).
but now the questions are :
edit :
before rebooting, i open dnstester.exe and block it, after that i can’t use it anymore (not valid win32 app)
after rebooting, i try dnstester again, got defense+ alert , block it, and then i can’t use it.
??? V3 will remember the actions taken until reboot.
[attachment deleted by admin]
Hi ganda
Yes, the first prompt you get from Defense+ is usually permission for explorer.exe to run whatever it is you’re trying to run.
Doesn’t work until after a reboot when blocked? It depends on what has been blocked. Often things “use” explorer in an attempt to access the default browser… now, if the the block is against explorer & something-else, then something-else will not work again until explorer is restarted (or the system is rebooted). This is because unremembered blocks are maintained for the “life” of the process and explorer (the system shell) does not automatically restart unless manually terminated or the shell crashes. You can restart explorer… but, that can upset some other applications. However, it should work after explorer has restarted.
hi Kail (:WAV) thx for the explanation.i get it now. :■■■■ cheers to that.
Downloading the test now… I just had to fix Comodo Firewall Pro, want to make sure it is working the way it is suppose to.
(L) (R) (S)
Test 2 opened up 10 Opera browser windows and told me that the next time it could be my credit card number.
:o :o :o
(edit)
However, according to GRC’s LeakTest, I’m secure.
10 browser windows!?! Credit card number? That doesn’t sound like Comodo’s CPIL test (Leaktest suite).
Yep, 10 browser windows.
If I type this message: This is dairyman using the CPIL test
It opens 10 browser windows like this:
1st Window = COMODO CPIL Test Website (with the word “the”)
2st Window = is.com
3st Window = dairyman.com
4th Window = using.com
5th Window = the.com
6th Window = CPIL.com
7th Window = test.com
There where obviously more words, but thats an example of what it did on my computer. But it probably isn’t the product - I’ve still got some spyware and viruses to remove.
Hello, I’ve been thinking of trying Cfw on 1 of my other systems (1 of which is currently running ESS, the other ZA), seems impressive and free too.
On my main system I have a lifetime subscription to Outpost Firewall Pro 4.0 (and I’m entirely happy with it) - it even passed all 3 of the CPIL tests so not sure about this quote:
While this application was being written, no other firewall than CPF 2.0 or later, was passing all of them. In our tests, all of them failed test 2 and test 3. Feel free to share your results with us.
Anyway, just thought I’d say hello and you may have another Cfw user soon as I have only 1 license for Outpost.
EDIT: Even more likely as I see Comodo is based in Manchester! (:WIN) (:WIN)