hi
i used the custom created rule for Firefox broswer “Allow IP out from any any MAC to any MAC where Protocol is any”. This custom rule was automaticlly created from Comodo after I answered the request “Firefox is trying to connect Internet” with ALLOW.
Comodo also has a predefined rule to webbroswers.
Which of these rules is most secure? Or should I even modify one ?
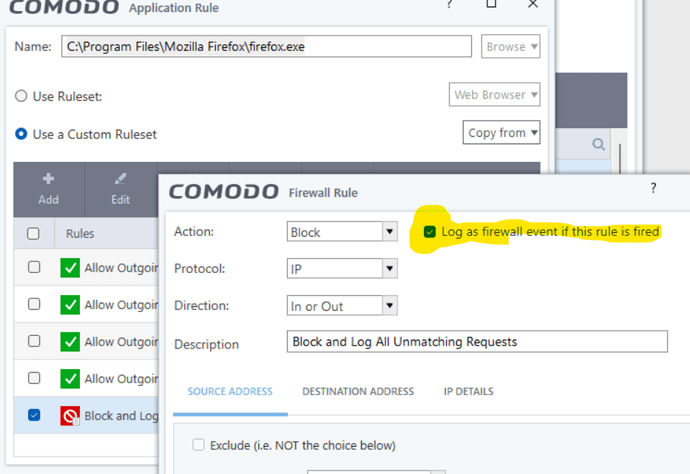
There’s no real need to add additional rules but you can use the Browser Ruleset.
which creates the below rules
But you may end up having to do some port whitelisting if you run into issue.
The below blocks occur with the web browser preset but no issue with browsing. Anyway, use what you prefer but there’s no specific need for strict rules as any unknown file or malware trying to abuse Firefox will be sandbox including that malware’s sub firefox processes.
i was using till now rhe custom created rule and from time to time I got “Firefox is trying ti receive connection” from some IPs. See the screenshot below.

I thing this was an intrusion try, right?
So I switched from the custom rule to the preseted Browser ruleset. And suddenly noticed in the Comodo logs many blocked access to many IPs like142.250.185.130, 34.120.195.249, 142.251.34.4, 216.58.206.66. These are all Google adresses right? Since that I noticed that Firefox i like flying on my old notebook, maybe I am wrong with this feeling - but could it be right?
Next question: so is the preset Browser rule better than the custom rule, because it may speed up the browsing? And what about the prevention beeing atacked from outside like shown in the screenshot - are both rule configurations delivering the same security be blocking the intrusions?
The predefined rulesets are described below from the help website. Although outdated, the information is still relevant.
Predefined rulesets
-
Although you could create a ruleset from the ground-up by configuring its individual rules, this practice would be time consuming if performed for every program on your system.
-
For this reason, Comodo provide a selection of rulesets according to broad application category. For example, the ‘Web Browser’ ruleset is designed for applications like ‘Internet Explorer’, ‘Firefox’ and ‘Chrome’.
-
Each predefined ruleset optimizes security for a certain type of application. Users can, of course, modify these predefined rulesets to suit their environment and requirements. For more details, see Predefined Rule Sets.
I don’t have some of the expertise as others here like @DecimaTech but your intrusion protection is primarily dealt through your router firewall but the preset browser rule blocks the unnecessary traffic so it may feel faster though I’ve not tested it for some time. Running a basic speed test I only see a fraction of a difference and these tests aren’t consistent but your probably good to go with the preset browser ruleset if you don’t mind the firewall log spam ![]()
I can turn off the logging of the blocked intrusions, so it wont spam the log ,right?
So to clarify for shorten: both preset Webbrowser ruleset and my custom allow rule “Allow IP out from any any MAC to any MAC where Protocol is any” are equal in terms of incoming connections, both will block all incoming traffic.
In terms of outgoing connections the preset Webbroser ruleset is sliightly better because it will also additionally block some specific traffic through specific ports to many Google bullsh*t. And so maybe speed up the browsing.
Is my logic right?
Yes, you can disable logging
As far as I understand it because the firewall blocks incoming from anything other than your router. See this article about setting for maximum security and usability though I heard the need for the additional options like Protocol analysis isn’t needed.
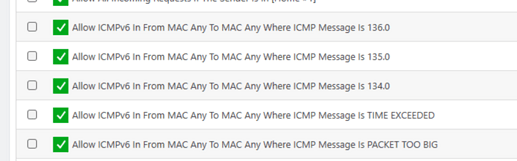
I have IPv6 filtering enabled as my ISP uses IPv6 so I’ve added a handful of necessary ICMP rules to allow it to work. Just time out, packet size and the three custom rules 134,135 % 136 to allow things line neighbour solicitation etc as explained in this article.
But there’s no real point in over complicating it.
What can be confusing is you’ll see blocks for programs you have alloweed after a restart and this is because the firewall takes time to load and it’ll block some connections until it’s fully loaded. For example after a full restart.