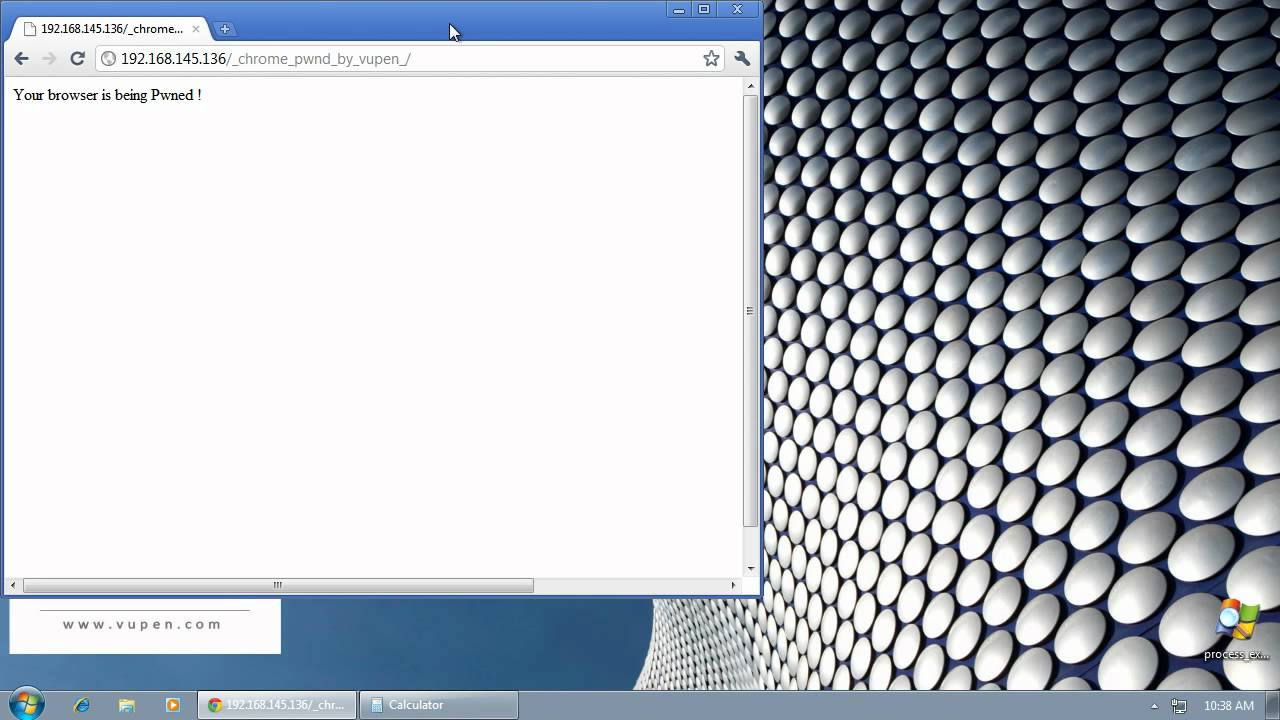
Here is a video how it works…I wonder if Dragon is affected…
Considering Dragon and Chrome share similar code bases, yes it would be affected.
I wouldn’t really call VUPEN ‘whitehats’ especially when they’re not for the people, they’re for the governments to use against the people.
Does CIS protect the computer in this case?, i.e., can the exploit be detected and stopped?
Is Comodo Dragon code affected?
Yes in any case…this does not feel good…I hope Chrome have a solution very soon…I would not feel comfortable If I knew the american government would have this backdoor…
VUPEN, which sells vulnerability and exploit information to business and government customers, does not plan to provide technical details of the attack to anyone, including Google.
Use Opera… security by obscurity… ![]()
Is this only for those that venture into unknown sites, usually unsafe sites, or how is the hack to work?
I believe that people that are safe won’t have a problem, yet some can be way too paranoid.
Well…good said…
But I also wonder… if most of the chrome exploits work on dragon aswell… would be nice to get some statistics… Cause I assume…Dragon as one further shield…
Your situation is a double-whammy. Normally, you will bring down Dragon because it’s a version behind Chrome, but now it’s a security concern on Chrome, so it’s a bring-down to both Chrome and Dragon.
Well, if we know how the hack can affect users, then I am up for that information. All they show is someone going to a certain address, or I don’t understand what they were doing, just that people shouldn’t get too worried that quick.
I am surprised that EricJH, being a Moderator, would suggest Opera.
Yet, I can’t complain, since Palemoon(Firefox) became my main not so long ago.
Thanks Erik. Seems we will never know.
Similar thread: VUPEN Whitehats Claim To Have Broken Chrome Sandbox |
Hopefully…the kernel is modified enough for it to not penetrate… would indeed be intersting if some one would test popular exploits… and see… if Dragons enhanced security is real or just PR.
Merged Similar Threads;
so this VUPEN thing sends vulnerabilities of users computers so that the gov can get in users computer?
also how do you get this VUPEN thing?
and if it is for the gov then why is it so unprofessional in saying your browser is getting pwned? you would think it would just do whatever in the background so no one will notice
VUPEN is the name of the group that engineered the exploit. Google is however calling it a Flash exploit, not a Chrome exploit.
does it do anything with the gov and how do you get infected with vupen
Vupen is a big security cy making research on vulnerabilities and developing solutions to remedy these vulnerabilities. Its clients are big cies and governments. This successful attack against Google Chrome which claimed to be nearly invulnerable is in my opinion just a good advertisement for them. But if they succeeded, probably others will too and that’s more scaring.
Here the site of Vupen Webmail: access your OVH emails on ovhcloud.com | OVHcloud
so they hack and then report the holes they found so that devs can fix them?