This error happens very often. What is the problem?
@megaherz33 use Cloud Verdict Customer Login | Xcitium Cloud Verdict to upload files to analysis
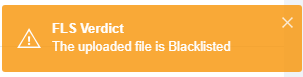
Here are some screenshots when the file is detected by CAMAS/XAMAS
I use it, but I wanted this site to work too.
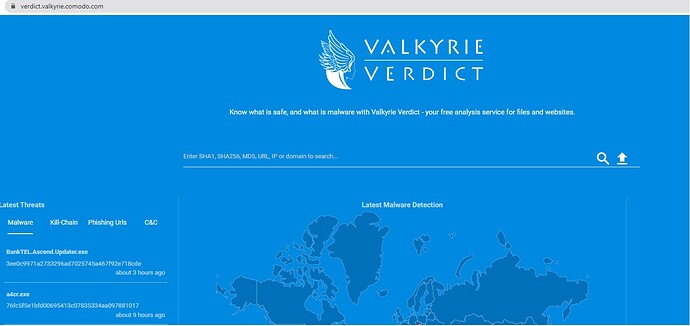
@megaherz33 for Valkyrie Verdict its a bug the error 500 is a bug
Error code 500 indicates that the request sent by the browser could not be processed for a reason that could not be identified. Unlike the 404 error where the problem is due to the content of the site, the 500 error indicates a problem that affects the server on which the site is hosted
@ZorKas and he wants the site to be fixed since you are a moderator with Xcitium you can fix it
@1807 Servers are the responsibility of administrators and developers
Moderators only manage messages and user behavior
I am the administrator of my site under SMF and during a problem on the server I open a ticket with the technical department mentioning the error codes and other data
@ZorKas so you reported the problem to the dev team to fix it
It is being reported via the Staff
FYI, real-time Malware detection requires an analysis report by SHA1 signature
I submit when I have time a signature package to the team concerned here
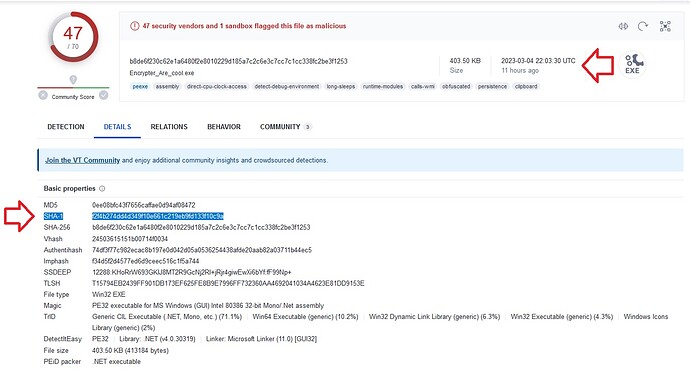
If we analyze my last submission, we realize that the signature
SHA1: f2f4b274dd4d349f10e661c219eb9fd133f10c9a
Not recognized by Valkirie for 11 hours but existing and threatening because it is Ransomware
So I create a file of 608 signatures (malware) to inform the Comodo Staff in order to analyze and update the databases
We must not forget that every minute are created Malware by hackers
Comodo by its defense on unrecognized files eliminates the threat by the container previously coupled with antivirus detection (base)
ZorKas
@1807 Problem immediately reported to Staff
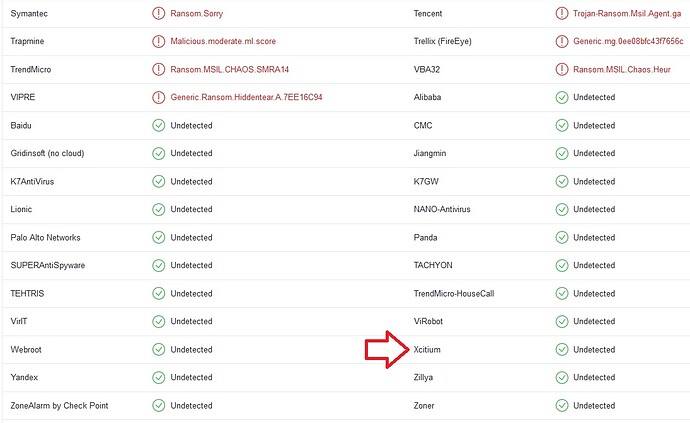
@ZorKas Xcitium uses also VirusScope in container which is Static and Dynamic Analysis and it gets detected too
@1807 Primary detection (unknown file detection) is the first level by Comodo
Does it have to be activated (ViruScope), it’s an option
Viruscope is necessarily linked to containment
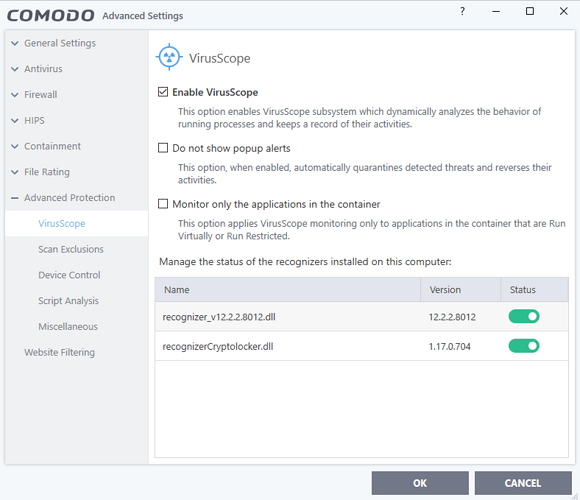
Default settings:
VirusScope Settings
VirusScope monitors running processes and alerts you to suspicious activity. You then have the option to quarantine the suspicious file and undo its activities.
-
Enable VirusScope - Activate VirusScope. If enabled, VirusScope monitors the activities of running processes and generates alerts if suspicious activity is detected. (Default = Enabled )
-
Do not show pop-up alerts - Whether CIS should show an alert if VirusScope detects suspicious activity. (Default = Disabled)
- If you choose not to show alerts then detected threats are automatically quarantined and their activities are reversed.
-
Monitor only the applications in the container - VirusScope only tracks the activities of processes that a running in the container. It will not track processes directly running on the host***. (Default = Enabled)***
-
Applications can be made to run in the container in two ways:
Run a program in the container on a ‘one-off’ basis. See Run an Application in the Container for more details.
Create a rule to auto-contain programs that match certain criteria. See Auto-Containment Rules for more details.
Manage the status of recognizers
-
VirusScope detects zero-day malware by analyzing the behavior and actions of an application.
-
If the detected behavior corresponds to that of known malware, then VirusScope will generate an alert which allows you to quarantine the application and reverse any changes that it made.
-
A ‘recognizer’ file contains the sets of behaviors that VirusScope needs to look out for.
-
If you disable a recognizer, VirusScope will no longer show an alert if an application exhibits behavior described by the recognizer.
-
We recommend most users to leave the ‘Status’ of recognizers at their default settings.
-
Advanced users, however, may want to try disabling recognizers if they are experiencing a large number of VirusScope false positives.
Comodo CIS is a very good insurance against Malwares ! ![]()
it certainly is, because it doesn’t rely on “detection for protection”…
any new executable file it doesn’t recognize, it enables “Kernel API Virtualization” (watch the video) which renders any damage harmless.
Hi megaherz33,
Thank you for reporting.
Could you please clear your cache and check ? as we don’t get this error.
(Refer the attached pic. Val.jpeg)
Thanks
C.O.M.O.D.O RT
@Melih
Hi Melih,
CIS has provided my eyes with protection insurance for more than 10 years
I thank you very much ! ![]()
This error appears when checking new files. With those that have been tested before, there are no problems.
Thank you @ZorKas
Yes including me, before CIS I used to deal with cleaning infected computers all the time… Thanks to CIS I have been infection free for A LONG TIME! ![]()