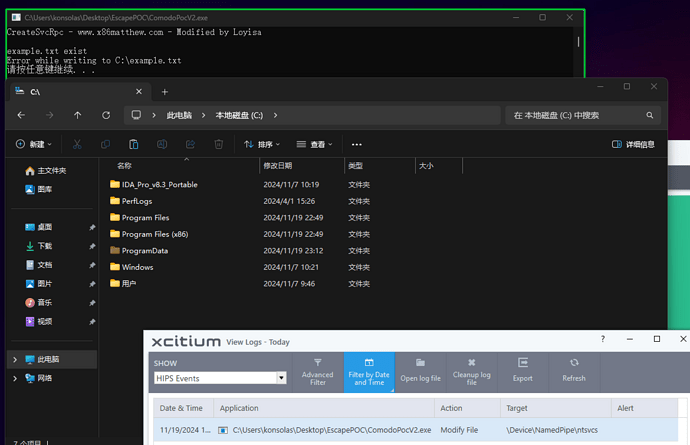
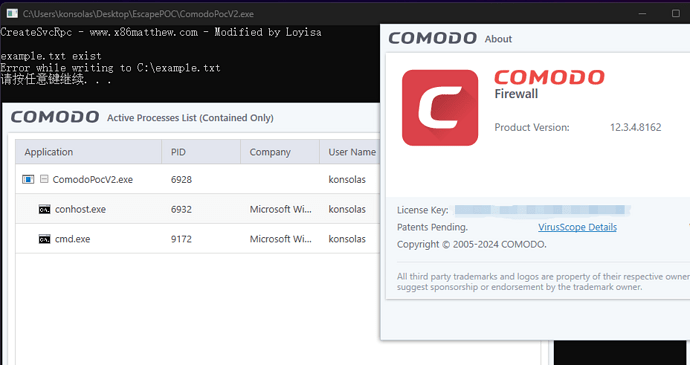
To tell the truth, it’s not Microsoft’s fault, this is a problem with CIS, which has a bug.
Because changing the UAC can cause damage to other applications, so it is not recommended to change it.
CIS is the one that has to fix this BUG from this POC Exploit.
This is an issue that affects other EDR applications, Symantec being the most prominent, so it is not specific to Comodo.
Every antivirus can be easily bypassed even if it’s Kaspersky I just infected him with Ransomware at AntivirusDefender malware series. The real issue is creating antivirus.
Yesterday, Xcitium Client Security – Windows (XCS Windows) seems to have been released with a fix for this in version 13.3.1 https://forum.xcitium.com/t/hotfix-release-notes-of-xcitium-enterprise-platform-agents-november-7-2024/18839 “Improvements in auto-containment security infrastructure.”. @Melih told here PoC bypass Auto-Sandbox CIS - #26 by Melih" everytime there is a legitimate workaround, we’ll work fast to fix it." and @ilgaz announced here New Version 12.3.3.8152 Available for Comodo Internet Security 2025 - #8 by ilgaz “we are working on it - stay tuned for another update as soon as possible.”, so they intend to roll out a fix for CIS as well.
To cover something as minor as this “bypass”, Comodo just needs a “Tweak” and not a “Fix”, so rolling out an update should be barely an inconvenience. Sadly (for others) protection from such things is going to be more problematic (they’ll probably just put it on ignore per SOP).
No, this isn’t a minor issue seeing that containment failed to prevent system changes, such as creating a new service that was not prevented from being created outside the container environment.
Comodo needs to perform code changes so that contained applications either can not access the service control manager through a named pipe, or to allow access but make sure it only stays within the containment.
If it wasn’t an issue to take serious then they would not have fixed it in xcitium client security. It is not as simple as making a tweak to the configuration, because even adding \device\namedpipe\ntsvcs to protected files did not prevent the bypass.
Also UAC doesn’t apply when not using restriction levels as the the default setting is to run virtually.
They fixed it in Xcitium ![]()
So far the POC has not been fixed in COMODO and XCITIUM.
When will it be fixed or is it easier to blame Microsoft?
@New_Style_xd you are wrong its fixed in Xcitium Client Security
Hello @Nik123,
Loyisa, confirmed with the test and the print that was made that the XCITIUM also has this failure and the POC bypasses the high containment.
No, it shows Xicitum fixed this exploit
@New_Style_xd I told you you were wrong but no you dont listen to me or Loyisa
Hello, sorry to everyone, now that I have a better look at the image, what you are saying is true.
Does anyone know when it will be fixed in CIS?
Hi Comodo fans,
We’ve just released an update that addresses the following issues:
1- Direct Upgrade from Existing Versions
2- Fix for Potential Containment Issue
For more details and download links for new version, please visit this post:
https://forums.comodo.com/t/new-version-12-3-4-8162-available-for-comodo-internet-security-2025/362887
Best,
The Comodo Team
@Loyisa Now the only thing is Xcitium needs to detect it with signatures so i suggest you to upload the POC to CAMAS(Comodo Valkyrie) for Static and Dynamic Behaviour Analysis
Now, in order for CIS to detect the Loyisa PoC + Ransomware, is it necessary to disable sending files to the Cloud? What story is that?
Really, all that remains for me to do is to wish the best wishes for 2025, hoping that this year 2025 will be the complete opposite of the year 2024, that is to say a great year for COMODO CIS.
A bizarre way for COMODO to solve a problem with another problem.
It would be easier to fix it without having to disable anything.