Hi,
Microsoft Pluton Security Processor
- Microsoft Pluton security processor
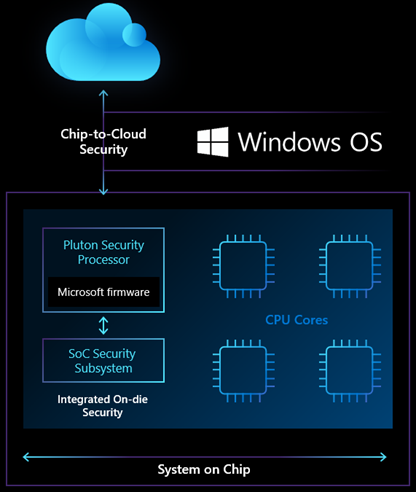
The Microsoft Pluton Security Chip is a chip-to-cloud security technology designed with Zero Trust principles at its core. Microsoft Pluton provides hardware-based root of trust, secure identity, secure attestation, and encryption services. Pluton technology is a combination of a secure subsystem that is part of the system-on-chip (SoC) and software created by Microsoft that runs on this embedded secure subsystem.
Microsoft Pluton is currently available on devices with Ryzen 6000 and Qualcomm Snapdragon® 8cx Gen 3 processors. Microsoft Pluton can be enabled on devices with pluton processors running Windows 11, version 22H2.
- What is Microsoft Pluton ?
Designed by Microsoft and engineered by silicon partners, Microsoft Pluton is a secure crypto processor built into the processor to provide security at the core of the code to ensure code integrity and the latest protection with updates provided by Microsoft through Windows Update. Pluton protects credentials, identities, personal data, and encryption keys. Information is much harder to remove, even if an attacker has installed malware or has full physical possession of the PC.
Microsoft Pluton is designed to provide Trusted Platform Module functionality as well as provide other security functionality beyond what is possible with the TPM 2.0 specification, and enables the provision of additional pluton firmware and system functionality operating over time via Windows Update.
Pluton builds on proven technology used in Xbox and Azure Sphere, and provides enhanced built-in security features for Windows 11 devices in collaboration with leading silicon partners.
The Pluton Security subsystem consists of the following layers:
Description
Material:
Pluton Security Processor is a secure element tightly integrated with the SoC subsystem. It provides a trusted runtime environment while providing the necessary encryption services to protect sensitive resources and critical items such as keys, data, etc.
Firmware:
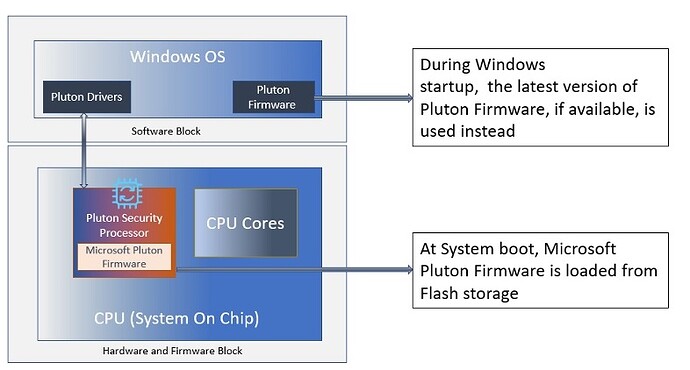
Microsoft-authorized firmware provides the required secure features and functionality, and exposes the interfaces that operating system software and applications can use to interact with Pluton. The firmware is stored in flash storage available on the motherboard. When the system boots, the firmware is loaded as part of the Pluton Hardware initialization. When Windows starts, a copy of this firmware (or the latest firmware obtained from Windows Update, if available) is loaded into the operating system.
Software:
Operating system drivers and applications available to an end user to enable seamless use of the hardware features provided by the Pluton security subsystem.
Firmware upload flow:
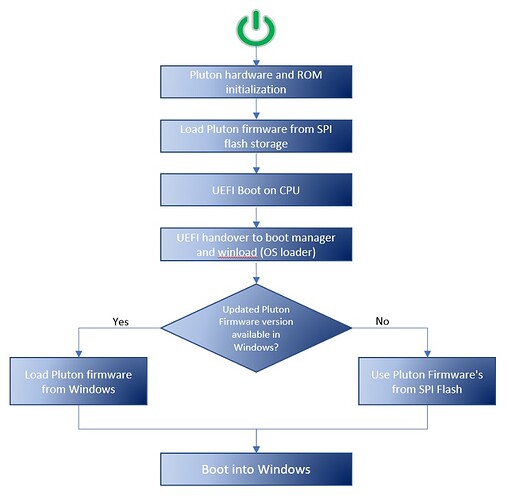
At system startup, Pluton hardware initialization is performed by loading the Pluton firmware from the Serial Peripheral Interface (SPI) flash storage available on the motherboard. However, when starting Windows, the latest version of the Pluton firmware is used by the operating system. If newer firmware is not available, Windows uses the firmware that was loaded during hardware initialization. The diagram below illustrates this process:
Knowing that the A.I (Artificial Intelligence) will grow and that hackers will certainly not miss it.
In the next 2 years (and future of course), the security of PC data will certainly be a considerable issue, hence the important reflection on the equipment to be acquired soon as well as the software, including security (hackers are already at work trying to intercept data via TPM).
ZorKas