Hello good people of the Comodo forum.
A YouTuber has posted a video he made of him testing Comodo CIS 11 against various samples of malware.
Whilst doing so he found that some files were able to be created outside of the Sandbox.
He then concludes that he does not give Comodo a verdict of a “clean sheet” due to the files being created by the malware outside of the sandbox.
However there is something to note here. At 1:07 in the video, the YouTuber decides to add his own script (the one that is executing the malware samples) to the ‘Ignore and Add to Exclusions’ list.
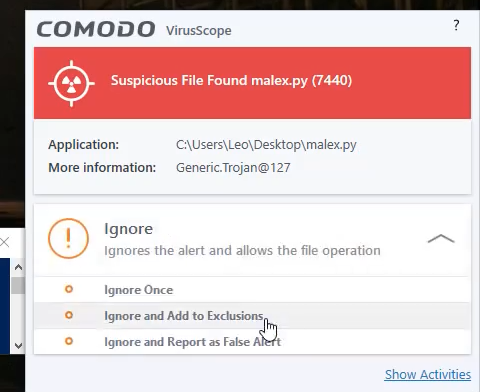
What do you think? A fair test? Or did his actions of adding his script to the ‘Ignore and Add to Exclusions’ actually enable the malware to write files outside of the sandbox?
I have included the link to the review below.
Fair. Comodo failed because one of the malware was rated as trusted in the cloud.
viruscope block or add exclusions antivirus?
Hi morphiusz, what makes you think that Comodo rated malware as trusted in the cloud?
Thanks.
Actually I think a test can’t be considered fair wherever someone clicks deliberately on “ignore” on a detection.
agree but there was a bypass in default settings cloud lookup because file/exe doesn’t sandboxed cause the file marked as trusted
sorry for bad english further details you can look https://malwaretips.com/threads/comodo-internet-security-11-review-test-vs-malware.86292/
antivirus testing or suites should be done in each separate protection module (there is always the possibility that one or more modules may fail). That’s why I’ve always used products comodo. For example: when I go to do some testing, disable firewall, hips, self-contention and keep the antivirus activated …
In short:
Only active antivirus, detection test;
Only active firewall, data leak test;
Only active HIPS, protection test;
Only Auto containment active, test protection system;
Only active viruscope, test protection against malware such as ransomwares.
This is how I do my tests
@liosant: Yes, but if you are performing a real-world test you should test the suite with all its components and protection modules on, not only one by one.
The test performed by TPSC was unaccurate and wrong performed by a tester point of view. He didnt even checked the containment menu in comodo…nor he tried to reset sandbox or to clean up temp files. He just used his (detected) .py script and gg. Bad.
Yes, but we must test in every possible possibility, when viewing the video I realize, that the viruscope quarantines the threats and how in this case the user can do it accidentally (allow a malware if executed in the machine);
I will cite as an example the tests that I did during the time I started using computers. Since then I have had experiences with most of the antivirus developers or security suites, and it was the only one that prevented the leak of passwords, emails …
Going back to the practice of security software tests, some when a module crashes or users and allows malware to infect the machine.
No suite is 100% safe (I know problems in most security suites and comodo is not perfect, but it provides us with excellent security)
Sorry my english
Hi mailmen,
This has already been posted here https://forums.comodo.com/news-announcements-feedback-cis/questionable-comodo-review-video-of-malware-files-being-created-outside-sandbox-t122640.0.html ![]()
Kind regards,
Reece