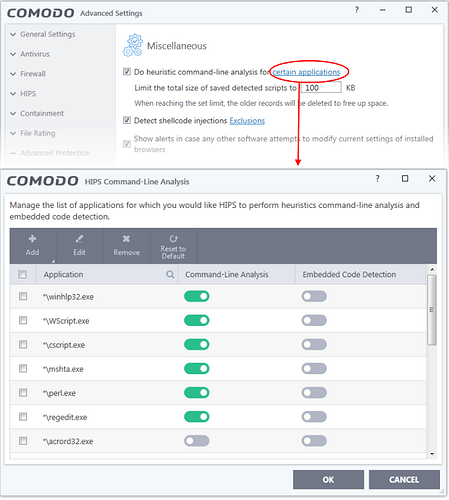
If a Ransomware use a Trusted file like Powershell, wscript, cscript, regsvr32, rundll32, mshta, bitsadmin, and etc… To run a bad Script, Will HIPS give a alert? I think not, because it is run from legitimate process…
If not, why don’t comodo Create a special Rules in HIPS for every legitimate files that often be used by Ransomware, so they can’t encrypt our files?
For example, like Eset: [KB6119] Configure HIPS rules for ESET business products to protect against ransomware (8.x–10.x)
Thank you…
Yes. You’ll get alerts for those. However, if you install another interpreter then you’ll have to “add support” for it.
Is that mean, every process inside this column will be intercept by HIPS Alert if they want to Encrypt our files, especially inside Protected Files and Folders?
First of all, it gets auto-sandboxed. If you add a folder to ‘Protected Files and Folders’ then its contents are not accessible.
If Auto-Containment is disabled, you get alert that it attempts to modify files (but not limited to such alert). If you add a folder to ‘Protected Files and Folders’ then you’ll get alert when it attempts to access it.