CIS and CCS/XCS are distinct products. While the company name can be flexible, it’s crucial not to conflate separate products as if they are merely rebranded versions of one another.
So does this mean that I am not protected by XCITIUM? how it should be?
Xcitium and CIS are very similar in it’s protection but Xcitium is for business networks and therefore requires additional features such as remote management and addditional analysis but the Comodo Clound and Xcitium cloud databases are the same.
e.g. Comodo Transparency Page & Xcitium Transparency Page contain the same data. If, for example, you run a live network at home covering several computers and a server running full time, like there is in a business environment, then maybe it’s worth looking at using Xcitium EDR but the protection itself at the end of the day is more or less the same. Your over thinking it and the setup you are using is bulletproof.
Hello friends, I want to clear some doubts.
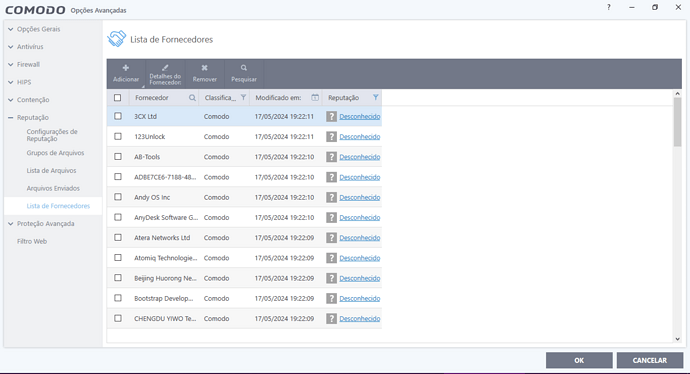
I’m here looking at lists of suppliers that are unknown to the CIS.
What I want to know is how do I get the CIS to check and confirm that the supplier is trustworthy, because there are some that have not been updated for more than 2 months.
You can add vendors yourself or lookup & submit those unknowns and they’ll evenutally get whitelisted…
Friend, the problem is that I sent everything, but I didn’t get a response, it was all unknown, even after it was sent.
Even though you said this: “You can add suppliers yourself or search and submit these unknowns and they will be whitelisted…”
It should be added automatically without me needing to include it in the whitelist
The CIS should do this loudly in doing this you don’t agree on this, because if it’s different it’s wrong
Files do get whitelisted and vendors added, just keep checking with the lookup. Sometimes it’s taken days or in some circumstances, If it’s causing issue on your machine or preventing something running, you can whitelist them yourself. Unknown files are automatically submitted and analyized in the cloud and CIS is just protecting you.
Does the timestamp of these blocks correlate with a restart of your machine or just happen while they are running? Is, for example, 3CX not working properly on your machine when you run it?
I haven’t restarted my machine for 12 days.
Do I need to restart the machine to update the CIS supplier list?
I’m not 100% sure but I think it comes with signature updates. Anyway, if your having issue with it, just manually add the vendor or whitlist the files. CIS does block some things on a re-start until it’s fully loaded which is why I asked whether you checked the timestamp of the blocks.
How does Comodo Internet Security beat Kaspersky’s AV and Firewall? How is it better and more secure?
I believe it only won because of the high containment, but I think the CIS is weak at detecting Malware
Guys, I checked this program and it’s clean. When I install it, the CIS doesn’t automatically let me know that it wants me to put it in HIGH CONTENTION.
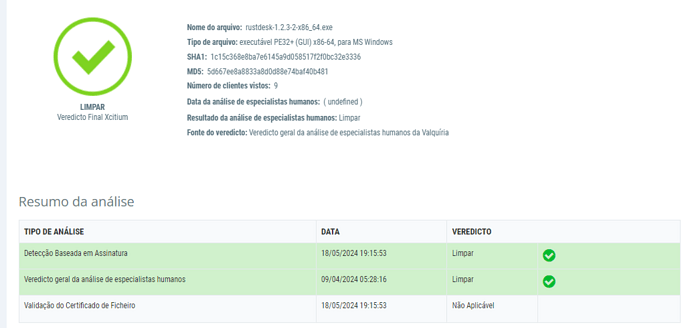
I wanted to know if this file really is reliable, and if so, why does CIS say it isn’t?
Nome do arquivo: rustdesk-1.2.3-2-x86_64.exe
Tipo de arquivo: executável PE32+ (GUI) x86-64, para MS Windows
SHA1: 1c15c368e8ba7e6145a9d058517f2f0bc32e3336
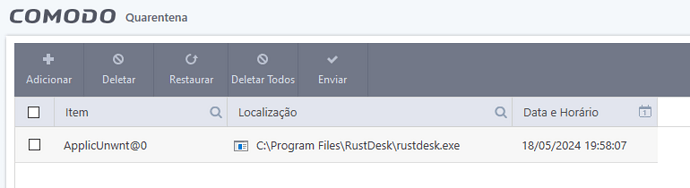
Look, my CIS is saying it’s a virus and sent it to quarantine.
Guys, I think the verdict was wrong, because this program is infected, just take the test at your CIS.
Valkyrie Verict for RustDesk.exe says the file isn’t signed.
VirusTotal has a few detections but says file is signed in the details.
Valquíria Verict says that the file is clean, when I installed it on my machine the CIS placed high contention.
except that the CIS said it was a VIRUS but the Valkyrie Verict LET IT PASS. There is something wrong with the images I posted.
Local (on your PC) and Valkyrie verdict are two different things. Can you post a screenshot of the log entry?
When evaluating endpoint protection or antivirus products, it’s crucial to consider their ability to detect three categories of files:
- Bad Files
- Good Files
- Unknown Files
Literally every competitor, focus on detecting “Bad Files” using a Default Allow method, meaning they allow all files unless they are specifically identified as harmful. This approach can be problematic because it’s impossible to detect 100% of bad files, leading to potential infections when unknown files turn out to be malicious.
Comodo stands out by detecting all three categories. For unknown files, we use our patented Kernel API Virtualized Containment technology. This means any unknown file is automatically isolated in a secure, virtual environment, preventing it from causing any harm even if it turns out to be malware.
Note: When an unknown file is contained, it is then sent to Valkyrie (a huge cloud platform in our Threat Labs) for analysis, where both AI and human experts work together to provide a “Trusted Verdict” for every file with your security in mind! That verdict is then sent back to your computer, so the unknown file becomes either a Known Good or Known Bad file.
This approach embodies our Zero Trust philosophy, where we assume no file can be trusted until proven otherwise. We don’t take risk by allowing an unknown run on your computer outside our Containment. You can read more about this concept in this Gartner report on Zero Trust.
For a visual explanation, you can watch Defaul Deny posture video.
Additionally, We are the only company offering full transparency with our statistics, which are publicly available on our Comodo Labs Statistics page. This level of transparency and our Zero Trust approach are key reasons why Comodo outperforms competitors.
Guilty Until Proven Innocent: The New Standard in Cybersecurity
Imagine it’s 10 PM, and a stranger knocks on your door. You invite them in, and they sit on your sofa for 24 hours. Can you be sure they are harmless just because they haven’t done anything bad yet? Of course not! This analogy highlights a crucial point in cybersecurity: absence of bad behavior doesn’t equate to trustworthiness.
In today’s cybersecurity landscape, many systems assume a file or code is safe unless it exhibits bad behavior. This “innocent until proven guilty” approach is fundamentally flawed. Instead, we need to adopt a “guilty until proven innocent” stance. Until a piece of code is verified as safe, it should run in a controlled, virtualized environment. This prevents potential damage if the code turns out to be malicious.
Traditional methods like antivirus, AI, and machine learning focus on detecting bad behavior, but their inability to identify a threat doesn’t guarantee safety. Allowing unknown code to execute simply because it hasn’t been flagged as malicious is a recipe for disaster. The numerous cybersecurity breaches in the news are evidence of this outdated approach’s failure.
It’s time to change our mentality and protect ourselves differently. Embrace the “guilty until proven innocent” standard to ensure robust cybersecurity.
And that is Zero Trust !
Sorry, friend, I removed all the entries to get around the virus that was installed. I ran Kaspersky on my machine, and it removed everything.
Unfortunately, Valkyrie’s verdict isn’t all that, it let a virus pass. Kaspersky eliminated it after I installed it.
Can i have the SHA1 so the team can check and blacklist it?
This one is clean, but I did the installation and the CIS placed it in Containment as it was with the verdict as clean, I took it out of containment and was infected. I had to use Kaspersky to clean the virus. That’s why I think the Valkyrie has a virus inside it. Just take the SHA and put it in the total virus, there are some antiviruses that put it as a virus, CIS itself identified it as Malware.
SHA1: 1c15c368e8ba7e6145a9d058517f2f0bc32e3336