Comodo 2025 UEFI Ransomware bypass AntivirusDefender 8.0 bypass all antiviruses in 2024 (youtube.com)
HydraDragonAntivirus/AntivirusDefender8.0: Comdoo bypass with UEFI ransomware. Ransomware FUD. Malicious bootmgfw.efi source code: https://github.com/HydraDragonAntivirus/AntivirusDefender7.0-UEFIRansomware
Fully Undetectable Malware. Bypassing Comodo. You can find repo at Github.
Vulnerability at Comodo.
It seems that it’s implemented by replacing the OS‘s bootmgfw.efi file with the malicious one.
C:\Windows\System32\cmd.exe "/min /c start mountvol x: /s && attrib +r +h +s && copy bootmgfw.efi x:\efi\boot\microsoft\bootmgfw.efi /Y
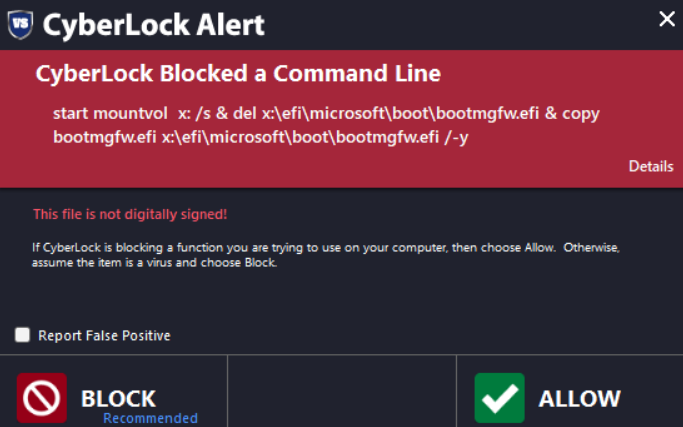
Yes. I fixed few commands. C:\Windows\System32\cmd.exe "/min /c start mountvol x: /s && del x:\efi\microsoft\boot\bootmgfw.efi && copy bootmgfw.efi x:\efi\microsoft\boot\bootmgfw.efi /-Y
If Comodo’s Containment was actually bypassed, we are vulnerable, the Comodo team needs to fix this flaw, which was posted by our friends here on the forum.
Nothing happens in Windows 10.
Nagrywanie 2024-06-10 205131.mp4
It didn’t even replace the original efi
Generally speaking, as Andy Ful from MT has already shown, most of the security will succumb to Lolbins
If anyone can do more tests, to find out whether the self-restraint was actually bypassed, yes or no.
Whoever can do more tests will be good. with both Windows 10 and Windows 11.
We need several results.
So it’s a link to an elevated cmd script disabling CIS Containment service as Andy Ful demonstrated earlier this year bu,t can you show a downloaded executable creating such link and executing it without being protected by CIS? @XylentAntivirus
Comodo can protect against these with enabling Embedded Code Detection in Script Analysis for cmd but it can be done by any of the LOLbins of which there are hundreds. Enabling it for cmd it causes a lot of FP issues that affect usability.
I run CyberLock along side CIS so automatically blocked with that as below or easily blocked if some system hardening used via one of Andy Ful’s tools.
Would love for CIS’s services protection or included in script anaylis heuristics.
In reality, an unknown executable would have to be downloaded and then such a script created and executed and then malware launched after reboot to infect the system so perhaps the author can provide such an example.
Indeed this shouldnt be regarded as Containment scenario at first place. Running a cmd with admin privileges using already planted files is nothing with Containment. If we want to consider real-time scenario, the dropper will already be contained so bootmgfw.efi files will not persist on disk anyway.
Also as @EricCryptid said script analysis will also protect these scenarios even those planted file cases.
Be careful when viewing the “Bypass” videos. Some run links to stuff somehow dropped onto a system, some will run cmd scripts without Script Analysis being enabled, and some are just duds.
I guess I broke something while editing code.
Okay I find the problem. I executed from cmd .lnk file that’s why he worked. I should find the reason of this.
Write better to VT why they show AV, FP engines.
Also try not to suggest what VT will show, because without experience you will mislead uninformed users.
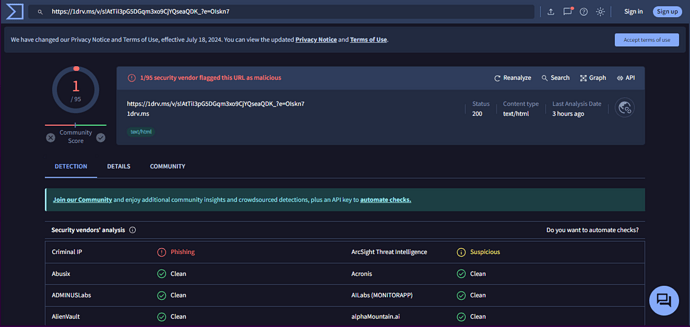
I don’t know why 1drv.ms pop up while I put the link.
I only showed what the VT reports. not my fault. I just asked a question.
Spoiler: Only AntivirusDefender6.6.6 working (youtube.com) It didn’t work actually if you don’t run at cmd.