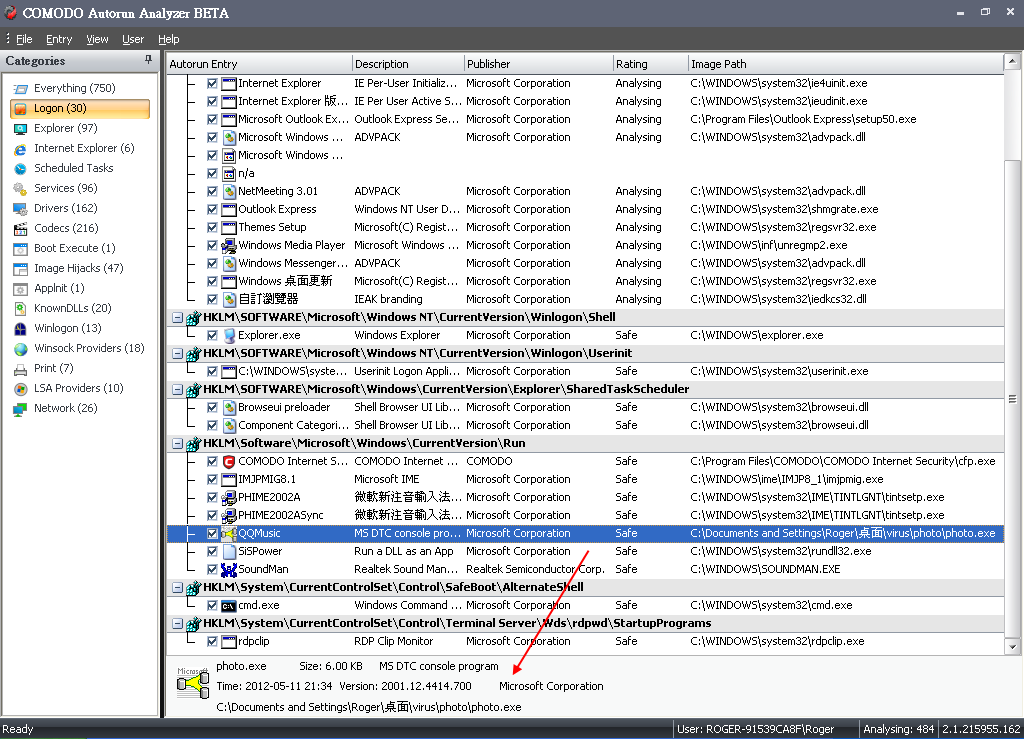
I double click on the photo.exe.
It can terminate the existing process of QQ IM software.
2.Then, I restart QQ IM and type some words on the window of it.
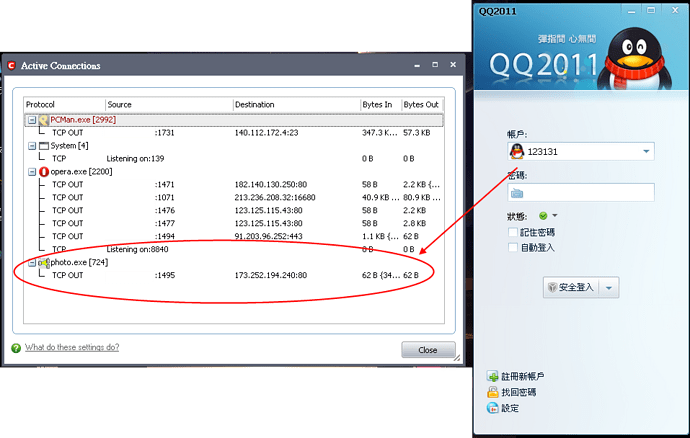
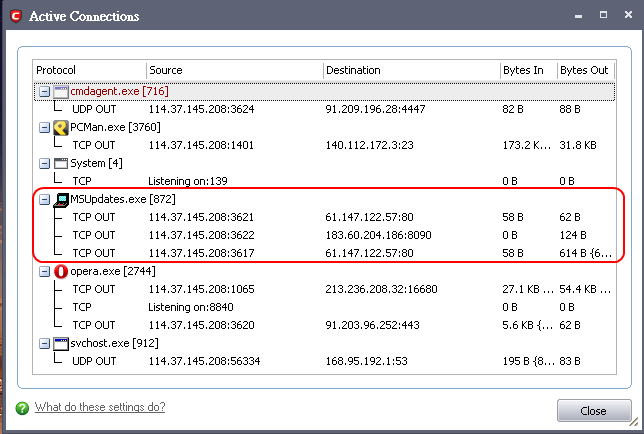
The photo.exe can connect to the internet.
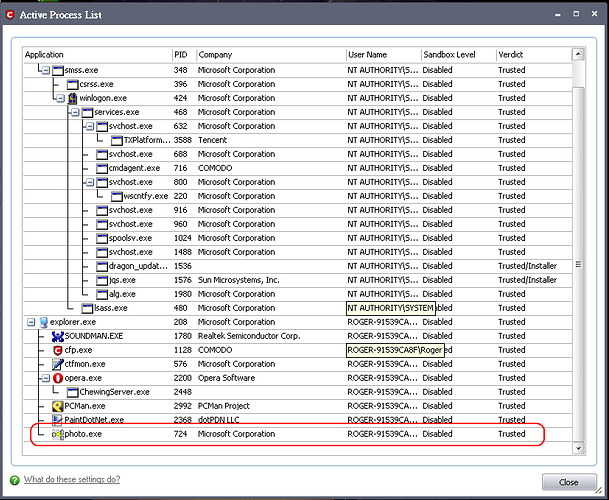
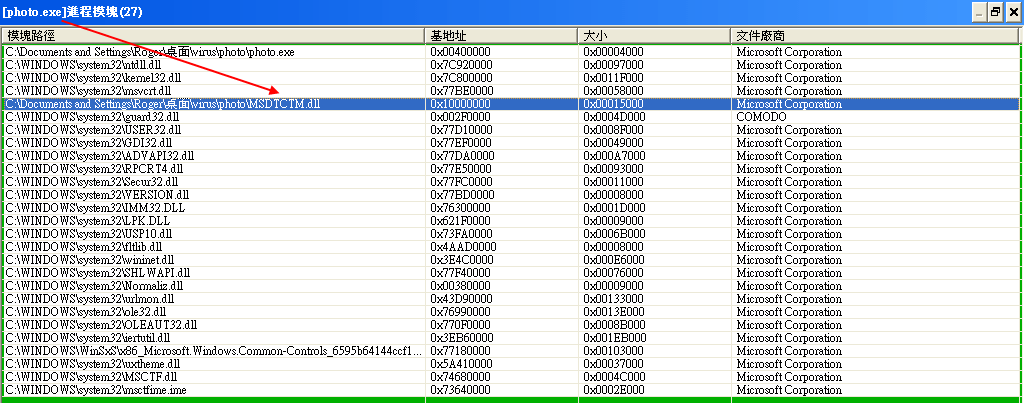
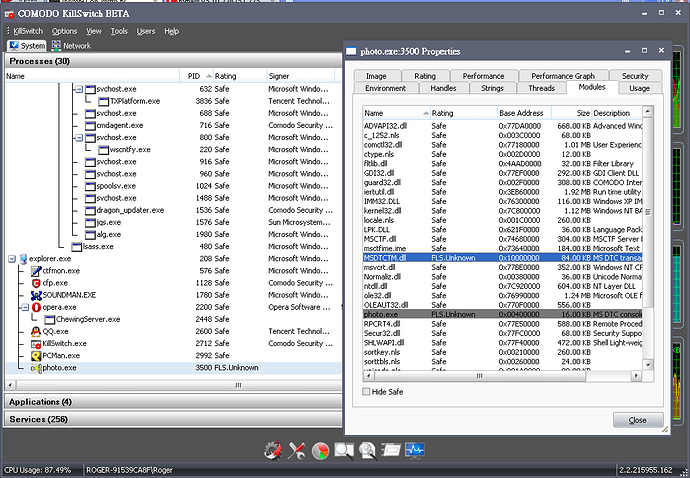
3.comodo trusts the photo.exe which is injected with the MSDTCTM.dll.
4.The malware creates an autorun entry.
5.environment:
Windows XP SP3 32bit
do you have a virustotal of the photo.exe
can you open up kill switch and show me the active processes and then show me the associated dll’s with the photo.exe and QQ?
I double click on the photo.exe.
It can terminate the existing process of QQ IM software.
2.Then, I restart QQ IM and type some words on the window of it.
The photo.exe can connect to the internet.
3.comodo trusts the photo.exe which is injected with the MSDTCTM.dll.
4.environment:
Windows XP SP3 32bit
Hi a256886572008,
We are looking into this issue and provide a fix as soon as possible.
Thank you for reporting it!
Regards,
2.The malware puts a transparent window on the window of QQ IM.
So, it can connect to the internet, after the user types some words on that.
Аlmost half a year has passed since the first reports of this problem.https://forums.comodo.com/news-announcements-feedback-cis/allegation-of-comodo-defence-plus-byapssed-by-zeroaccess-rootkit-t79079.0.html
fake5
May 12, 2012, 9:39am
8
:-TU :-TU :-TU
Oh well… The chances of you walking into such malware is low same as ransom…
Current CIS can likely be made to stop this with D+ rules… will it cut into compatibility and stability? maybe.
Automatically sandbox process whose modules contain unrecognized files ?
Well maybe not like that with the current version thats more 6.0. I mean I could make a custom rule for Photo.exe to prevent it from getting infected.
In Defence+, Would changing from “partially limited” to “limited” solve this?
comodo would still trust the malware.
pykko
May 16, 2012, 5:38pm
15
This is a very serious issue. Is any Deve looking into it ?
so from what I can tell this is what is happening, a trusted file is loading malware into memory and if the AV does not catching it, it would bypass. Is that what you are saying?
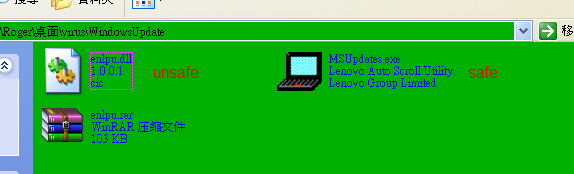
another sample:
enlpu.dll (50.1MB)https://valkyrie.comodo.com/Result.html?sha1=929f6b272fc399fb1abc06801d52e844685f83fd&&query=0&&filename=enlpu.rar
MSUpdates.exehttps://valkyrie.comodo.com/Result.html?sha1=f7f57137a029457f132ae63c1b41eac24ac21524&&query=0&&filename=msupdates.exe
2012-05-22 15:14:22 C:\Documents and Settings\Roger\桌面\virus\WindowsUpdate\MSUpdates.exe Sandboxed As Partially Limited
2012-05-22 15:14:24 C:\Documents and Settings\Roger\桌面\virus\WindowsUpdate\MSUpdates.exe Modify Key HKUS\S-1-5-21-1993962763-796845957-1801674531-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable
2012-05-22 15:14:24 C:\WINDOWS\Explorer.EXE Sandboxed As Partially Limited
2012-05-22 15:14:25 c:\hds1.exe Sandboxed As Partially Limited
2012-05-22 15:14:27 C:\WINDOWS\system32\conime.exe Sandboxed As Partially Limited
2012-05-22 15:14:27 c:\hds2.exe Sandboxed As Partially Limited
2012-05-22 15:14:30 c:\hds3.exe Sandboxed As Partially Limited
2012-05-22 15:14:30 C:\Documents and Settings\Roger\桌面\virus\WindowsUpdate\MSUpdates.exe Access Memory C:\WINDOWS\explorer.exe
2012-05-22 15:14:44 C:\WINDOWS\system32\userinit.exe Modify Key HKUS\S-1-5-21-1993962763-796845957-1801674531-1003\Software\Microsoft\Windows NT\CurrentVersion\Windows\Device
2012-05-22 15:14:52 C:\WINDOWS\system32\userinit.exe Access COM Interface \RPC Control\spoolss
turning security to proactive will stop that, in the stock internet security mode the firewall lets anything out basically.
Because CIS trusts the MSUpdates.exe, it was bypassed by the malware.
MSUPdates.exe is not trusted as it gets sandboxed. Or did you sandbox if manually for testing or instruction purposes?