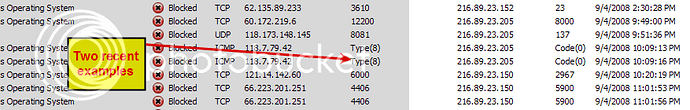
When I look at my event log, I see some intrusion attempts listed as “Type (8)” on the Source Port and “Code (0)” on the Destination Port, instead of port numbers. I’ve searched help and this board, but can’t find anything on these. What does this mean??
Hey bob, Have a look here.
So this means somebody pinged me?? Since all my ports are stealth, I assume then that this ping was a “shotgun”??
Can you please post a screen shot of your event window and are you behind a router?
Gruee155 is more experienced in this, I’ll message him to have a look at this for you.
That screenshot wasn’t too clear. I’ve cropped it.
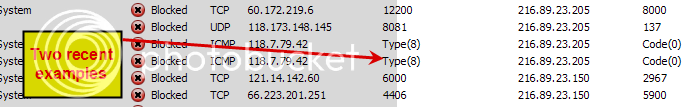
If I need to resize let me know.
Wiki already explained it. Type 8 Code 0 is Echo Request, which is essentially a ping request from the outside. As you suspected, CFP blocked this request (which it does based on default rules anyway).
I get these all the time when I use uTorrent. It’s also a frequent tool used by gamers to test latency etc.
Soyabeaner,
Got it . . . thanks.
And was I right about it being random?? I mean, if they can’t see me (stealth), it must’ve been the “shotgun” scan for Domain Names that did it, and not a ping based on knowing my domain name/number.
Guess so. But anyone you connect to will know that you are online and can ping you back.
Yet another reason to have CPF, huh?? So when you connect to somebody and they ping you, do they get a message that their ping was blocked?? Or is it?? If you connect to somebody through your browser, then is their ping allowed??
Hmmmmmm . . . guess I need to read up on basic firewall stuff. I thought I understood the basics, but apparently I need more study.
Once a ping request reach CFP they cannot ping you if there is a global rule to block PING (it does by default).
You can block either Inbound echo requests or outbonds echo replies.
Make sure that you have the latest CFP verion.
Time to RTFM. But I can only find a user manual for version 2.3 ( CONTACT US - Comodo: Cloud Native Cyber Security Platform ) and I have 3.025.378 (is that the latest?). Is this user manual for version 2.3 sufficient for the version I have, or is there an updated manual for my version??
These are the latest version available at the moment. :-TU
you can test yourself by typing cmd in the start > run menu box > in the command prompt, type ping comodo.com
the results should be 4 request time outs
Yes, I did get the 4 requested time outs, but only after I got an alert and said to block it. Is that the way it should have worked, or should it just have gone immediately to the ping time outs without the alert??
It work this way if you run ping. But in this case the ping command send an Outbond echo request (ICMP 8.0).
According to the log entry you reported you altready block Inbound echo requests (someone pinging you from internet).
Yes, but that was to show you want the other side would see had they attempt to ping something/someone’s PC that blocks pings. BTW, BobJam, you were supposed to allow those alerts from CFP because it was you who did the pinging out (:LGH)
Hey Soyabeaner,
But then if I allowed that particular alert it would have failed the GRC Leak Test . . . NO??
In fact, I just tested it. I got the Firewall alert, allowed Leak Test, and it penetrated. But when I block it (on the alert), it passes. Am I doing something wrong??
Nope if you ping someone and you have a global rule to block incoming ping requests no one should be a ble to ping you.
Can you explain what you did step by step?
Please attach also a CFP config report.