Hello Radaghast,
Here you go. It’s a bit long and messy :D. Thanks for your assistance so far:
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\user 1>netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 808
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:33116 0.0.0.0:0 LISTENING 3480
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 496
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 1004
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 1068
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 596
TCP 0.0.0.0:49156 0.0.0.0:0 LISTENING 580
TCP 0.0.0.0:49157 0.0.0.0:0 LISTENING 1484
TCP 127.0.0.1:10000 0.0.0.0:0 LISTENING 3480
TCP 127.0.0.1:49163 127.0.0.1:49164 ESTABLISHED 208
TCP 127.0.0.1:49164 127.0.0.1:49163 ESTABLISHED 208
TCP 127.0.0.1:49165 127.0.0.1:49166 ESTABLISHED 208
TCP 127.0.0.1:49166 127.0.0.1:49165 ESTABLISHED 208
TCP 192.168.1.2:139 0.0.0.0:0 LISTENING 4
TCP 192.168.1.2:49162 91.198.117.130:443 CLOSE_WAIT 1916
TCP 192.168.1.2:49362 74.125.236.87:443 TIME_WAIT 0
TCP 192.168.1.2:49407 74.125.236.87:443 TIME_WAIT 0
TCP 192.168.1.2:49409 74.125.236.87:443 TIME_WAIT 0
TCP 192.168.1.2:49410 74.125.236.87:443 TIME_WAIT 0
TCP 192.168.1.2:49411 74.125.236.87:443 ESTABLISHED 208
TCP 192.168.1.2:49412 74.125.236.87:443 ESTABLISHED 208
TCP 192.168.1.2:49413 74.125.236.82:443 TIME_WAIT 0
TCP 192.168.1.2:49415 209.85.231.132:443 TIME_WAIT 0
TCP 192.168.1.2:49416 74.125.236.87:443 ESTABLISHED 208
TCP 192.168.1.2:49427 74.125.236.93:443 TIME_WAIT 0
TCP 192.168.1.2:49461 74.125.236.80:80 TIME_WAIT 0
TCP 192.168.1.2:49474 91.199.212.149:80 TIME_WAIT 0
TCP 192.168.1.2:49476 91.199.212.149:80 TIME_WAIT 0
TCP 192.168.1.2:49477 91.199.212.149:80 TIME_WAIT 0
TCP 192.168.1.2:49487 173.174.231.111:51413 SYN_SENT 3480
TCP [::]:135 [::]:0 LISTENING 808
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:5357 [::]:0 LISTENING 4
TCP [::]:33116 [::]:0 LISTENING 3480
TCP [::]:49152 [::]:0 LISTENING 496
TCP [::]:49153 [::]:0 LISTENING 1004
TCP [::]:49154 [::]:0 LISTENING 1068
TCP [::]:49155 [::]:0 LISTENING 596
TCP [::]:49156 [::]:0 LISTENING 580
TCP [::]:49157 [::]:0 LISTENING 1484
UDP 0.0.0.0:500 : 1068
UDP 0.0.0.0:3544 : 1068
UDP 0.0.0.0:3702 : 1220
UDP 0.0.0.0:3702 : 1220
UDP 0.0.0.0:3702 : 3080
UDP 0.0.0.0:3702 : 3080
UDP 0.0.0.0:4500 : 1068
UDP 0.0.0.0:5355 : 948
UDP 0.0.0.0:33116 : 3480
UDP 0.0.0.0:55819 : 1220
UDP 0.0.0.0:60260 : 3080
UDP 0.0.0.0:60266 : 1220
UDP 127.0.0.1:1900 : 3080
UDP 127.0.0.1:60265 : 3080
UDP 192.168.1.2:137 : 4
UDP 192.168.1.2:138 : 4
UDP 192.168.1.2:1900 : 3080
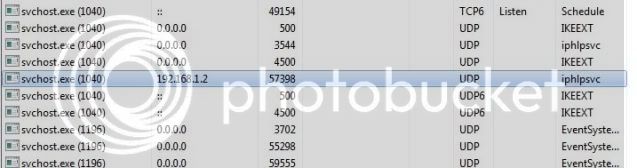
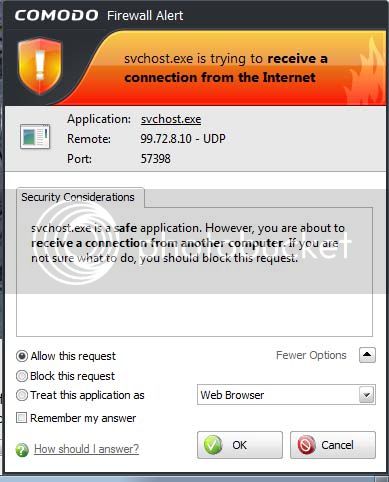
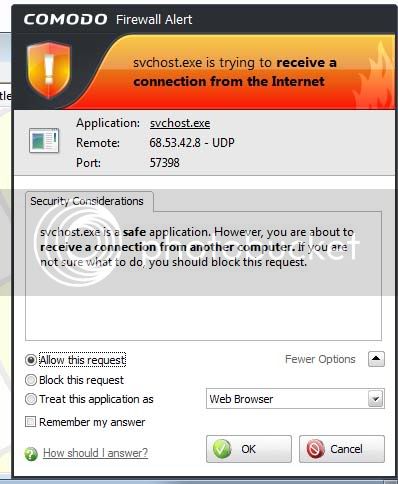
UDP 192.168.1.2:57398 : 1068
UDP 192.168.1.2:60264 : 3080
UDP [::]:500 : 1068
UDP [::]:3702 : 3080
UDP [::]:3702 : 3080
UDP [::]:3702 : 1220
UDP [::]:3702 : 1220
UDP [::]:4500 : 1068
UDP [::]:5355 : 948
UDP [::]:33116 : 3480
UDP [::]:55820 : 1220
UDP [::]:60261 : 3080
UDP [::]:60267 : 1220
UDP [::1]:1900 : 3080
UDP [::1]:60263 : 3080
UDP [fe80::70e2:af3a:5d39:c355%10]:1900 :
3080
UDP [fe80::70e2:af3a:5d39:c355%10]:60262 :
3080
C:\Users\ user 1>tasklist /svc
Image Name PID Services
========================= ======== ============================================
System Idle Process 0 N/A
System 4 N/A
smss.exe 304 N/A
csrss.exe 452 N/A
wininit.exe 496 N/A
services.exe 580 N/A
lsass.exe 596 ProtectedStorage, SamSs
lsm.exe 608 N/A
svchost.exe 728 DcomLaunch, PlugPlay, Power
svchost.exe 808 RpcEptMapper, RpcSs
cmdagent.exe 900 cmdagent
svchost.exe 948 CryptSvc, Dnscache, LanmanWorkstation,
NlaSvc
svchost.exe 1004 Audiosrv, Dhcp, eventlog,
HomeGroupProvider, lmhosts, wscsvc
svchost.exe 1040 AudioEndpointBuilder, CscService, Netman,
PcaSvc, SysMain, TrkWks, UxSms,
WdiSystemHost, wudfsvc
svchost.exe 1068 AeLookupSvc, Appinfo, gpsvc, IKEEXT,
iphlpsvc, LanmanServer, MMCSS, ProfSvc,
Schedule, SENS, ShellHWDetection, Themes,
Winmgmt, wuauserv
svchost.exe 1220 EventSystem, fdPHost, netprofm, nsi,
WdiServiceHost, WinHttpAutoProxySvc
SbieSvc.exe 1280 SbieSvc
spoolsv.exe 1612 Spooler
svchost.exe 1656 BFE, DPS, MpsSvc
DTSRVC.exe 1764 DTSRVC
pdisrvc.exe 1800 PdiService
psia.exe 1916 Secunia PSI Agent
svchost.exe 1948 StiSvc
svchost.exe 1484 PolicyAgent
svchost.exe 3080 FDResPub, FontCache, SSDPSRV, upnphost
csrss.exe 2348 N/A
winlogon.exe 2136 N/A
dwm.exe 2920 N/A
explorer.exe 3104 N/A
taskhost.exe 2828 N/A
cfp.exe 3472 N/A
wmpnetwk.exe 3960 WMPNetworkSvc
svchost.exe 2680 WinDefend
firefox.exe 208 N/A
TrustedInstaller.exe 3796 TrustedInstaller
plugin-container.exe 3944 N/A
uTorrent.exe 3480 N/A
WINWORD.EXE 3860 N/A
audiodg.exe 712 N/A
cmd.exe 1552 N/A
conhost.exe 2704 N/A
tasklist.exe 1296 N/A
WmiPrvSE.exe 552 N/A
![]()
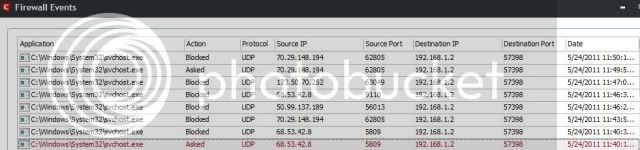
![]()