Literally ended the CIS ![]()
Hello. Dear New_Style_xd, I do not have the opportunity to view this video. if it’s not difficult to comment on this video and your words “Literally put an end to the CIS”
Hello my friend, a person who can speak with all the details, and our friend @XylentAntivirus
As he made the video he can speak with more authority on the subject. ![]()
@XylentAntivirus Could you explain in detail what really happened that the CIS was bypassed.
As you were the creator of the video, we want to know in detail. ![]()
Comodo can’t contain LNK files also when you scan LNK files it scans real file path not LNK file. Comodo can’t contain LNK files unless you manually contain it. So I can run the payload but when I make service with .exe Comodo contains it of course. But when I make service with driver it can’t contain it. But there problem. LNK files works on real paths so I need to write very short code to detect where driver located. Because when you write long code LNK file doesn’t accept it. So I used where then find the driver location then create the service. I can add shutdown -r -t 10 of course but that’s just makes LNK file more longer. Comodo generally can’t detect LNK malwares.
Thank you for your clarification. What about other antiviruses?
They can detect LNK file but can’t detect this, at least Kaspersky and Bitdefender.
Siradankullanici/0KBAttack: Malicious attack using empty files with its name to generate and execute from non-malicious code
Files with the .LNK extension are shortcuts to installed applications. If the association of .LNK files is damaged, it is possible that when opening applications, malicious code is executed, with the aim of controlling your system or personal data.
Comodo monitors launched applications but not LNK files that are not ID (process)
Hello, good afternoon,
I had a question when you said that “Comodo monitors applications that are started, but not LNK files that are not ID (process)”
Does this mean that we are at risk with LNK?
Thank you!
LNK is a filename extension for shortcuts to local files in Windows. LNK shortcuts provide quick access to executable (.exe) files without requiring the user to access the full path of the program.
Shell Link Binary File Format (.LNK) files contain metadata about the executable file, including the original path to the target application.
Windows uses this data to support launching applications, chaining scenarios, and storing application references in a target file.
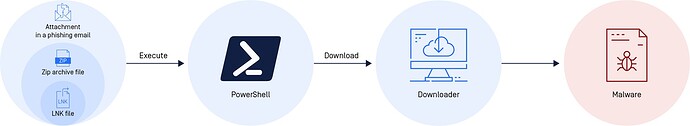
Since LNK files provide a convenient alternative to opening a file, threat actors can use them to create script-based threats. One such method is to use PowerShell.
Threat actors can insert a malicious script into the PowerShell command in the target path of the LNK file.
Reminder:
Comodo monitors all applications (process IDs) and understands scripts that are part of the system operator and therefore related to the LNK file
As an example of how Comodo deals with self-contained lnk malware, please view the video at 0.40 second mark:
Comodo and LNK malware example
Thank you my friend @ZorKas , as always trying to help the community, your explanations are very clear and objective.
I always learn from you. Even though sometimes I have difficulty understanding due to lack of knowledge of the COMODO System.
I haven’t used Comodo for many years like you, I’m starting to understand how CIS works with you.
I hope you continue helping all of us on the forum.
Hello @cruelsister How are you?
Thank you for sharing your knowledge. I watch a lot of your videos on YouTube.
I have some difficulty understanding your videos in ENGLISH, but I can still get an idea of what is happening.
Keep posting videos about CIS.
Comodo will detect the threat when launching the process through the LNK file
It detected launched powershell.exe commands file from LNK file but didn’t detected LNK himself. Yes Comodo can add LNK files into his signatures and detecting suspicious LNK files are easy for some antiviruses because they always flag long arguments of LNK no matter it was really malicious or not. The problem is Comodo can’t block my malware due to my reasons.If they are going to fix it would be too much harder to bypass Comodo Sandbox. I guess Comodo only doesn’t work at cmd.exe related LNK files if they are working very well.
Do you keep pushing? Do you find joy in this?
It seems clear to me that you are not getting what you seek… ![]()
Actually Comodo contains this quite well, as it will also with any lnk files containing extra code.
(where are all these Script-Kiddies coming from lately?)