System: XP SP3
Configuration: Internet Security
Mode: Safe mode
sandbox:enabled
Treat unrecognized files as: partially limited
Automatically quarantine threats found during scannig
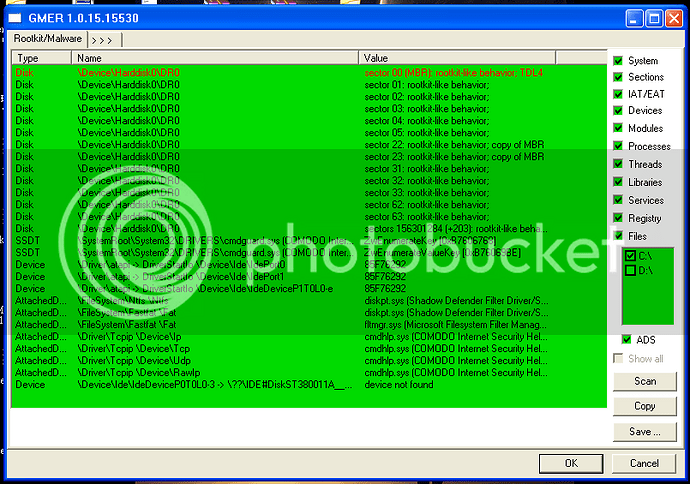
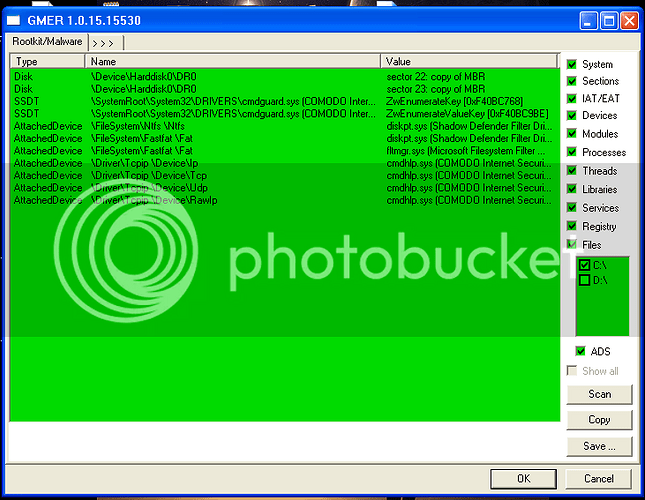
GMER:
defense+ logs:
2010-11-13 15:47:45 C:\Documents and Settings\Roger\桌面\virus\1289589994\1289589994.exe Sandboxed As Partially Limited
2010-11-13 15:47:46 C:\Documents and Settings\Roger\桌面\virus\1289589994\1289589994.exe Modify File C:\Documents and Settings\Roger\Local Settings\Temp\564.tmp
2010-11-13 15:47:53 C:\Documents and Settings\Roger\桌面\virus\1289589994\1289589994.exe Modify Key HKLM\SYSTEM\ControlSet001\Control\Session Manager\PendingFileRenameOperations
2010-11-13 15:49:01 C:\Documents and Settings\Roger\桌面\virus\1289589994\1289589994.exe Scanned Online and Found Malicious
antivirus logs:
2010-11-13 15:49:01 C:\Documents and Settings\Roger\桌面\virus\1289589994\1289589994.exe CloudBehavior.Suspicious[at]1 Detect Success
2010-11-13 15:49:01 C:\Documents and Settings\Roger\桌面\virus\1289589994\1289589994.exe CloudBehavior.Suspicious[at]1 Quarantine Success
CIMA:http://camas.comodo.com/cgi-bin/submit?file=4f63010477941a57f8e2e997b7c40136fc7a16dc2a2eafe86e99986cbb89075f
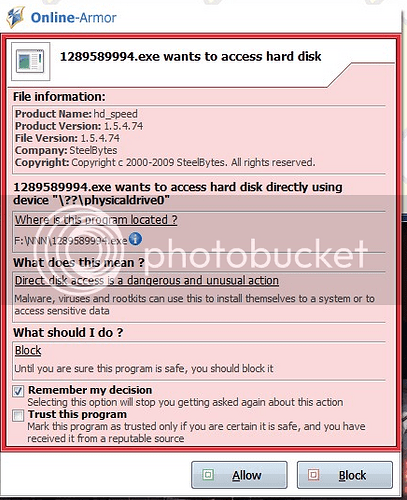
You should have gotten a pop up from CIS regarding a com interface asking for spooler access. Can you give me the file to test.
The virus was sandboxed automatically by COMODO.
There is no pop up from CIS.
I just tested stock install. Got an alert from D+ for a pseudo-com interface wanting to access windows print spooler service. Clicked block.
Then I get a AV alert from the cloud.
Lastly and alert from the firewall stating an malicious item wants to access the internet.
I just tested stock install. Got an alert from D+ for a pseudo-com interface wanting to access windows print spooler service. Clicked block.
Then I get a AV alert from the cloud.
Lastly and alert from the firewall stating an malicious item wants to access the internet.
Does CIS sandbox the virus with partially limited in your computer?
I test the virus again.
double click on the virus
1.Treat unrecognized files as partially limited
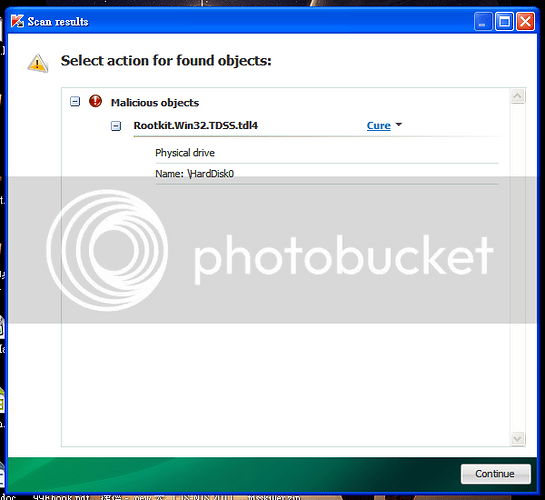
failed to block the action of the virus
2.Treat unrecognized files as limited
block the action of the virus successfully
IMO maybe they must add an heuristic danger indice for unknown PE like KIS :-TU
Exemple: indice less 15 => “autosandboxed” at “partially limited”
Executing all unknwon PE with the same limitations is not the best thing for me, bit it’s only my opinion
a256886572008, could you test this sample on x64? i’m curious :-TU
My computer is not a x64 system.
Syl
November 13, 2010, 11:03am
11
seems like another problem with x64 ^^;
MOVEAX
November 13, 2010, 11:05am
12
all can bypass comodo, it isnt a big issues 88)
Treat unrecognized files as partially limited
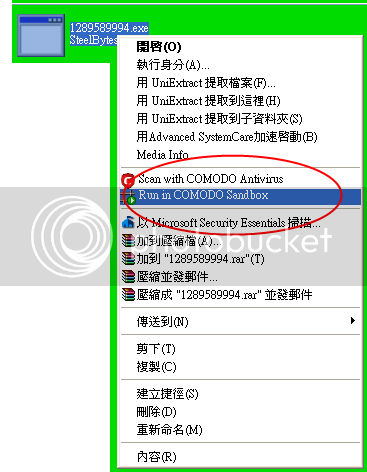
1.right click on the virus
2.choose “Run in COMODO sandbox”
3.COMODO blocks the action of the virus successfully.
defense+ logs:
firewall logs:
yes it does. I don’t know what you are doing but something is wrong with your install or settings. It is easily blocked in my computer with a stock install. I would check your D+ to make sure nothing is added to trusted lists and such.
Actually me and Egemen specifically worked on this issue to figure it out. What version of comodo are you running?
Syl
November 13, 2010, 5:28pm
15
languy99, do you use a 64 bits OS ?
no 32 bit test, just like the original test.
also a256886572008 please revise your post on wilders to include that it might be just your system. Next time I would not post any place else until someone here can confirm your claims.
read earlier post
i would like to test it but, here dont like virtual box and i dont feel like installing vmware player
yes it does. I don’t know what you are doing but something is wrong with your install or settings. It is easily blocked in my computer with a stock install. I would check your D+ to make sure nothing is added to trusted lists and such.
Actually me and Egemen specifically worked on this issue to figure it out. What version of comodo are you running?
1.System: 32bit XP SP3 Pro
2.language of the system: Traditional Chinese
3.version: 5.0.163652.1142 english
4.security software: comodo only
5.configuration: internet security
6.Treat unrecognized files as Partially limited
7.Mode: safe mode
I test another malware, comodo can pop up an elert for accessing COM interface.
But, comodo can not pop up an elert for this virus that access COM interface.
I did not test it in the VM.
no 32 bit test, just like the original test.
also a256886572008 please revise your post on wilders to include that it might be just your system. Next time I would not post any place else until someone here can confirm your claims.
Someone tests it in VirtualBox 3.2.10
system: Windows XP sp3 32bit (no update)
language of the system: Traditional Chinese
Partially limited → failed
limited → success
Another one does not test in VM.
language of the system: simplified Chinese
Partially limited → success