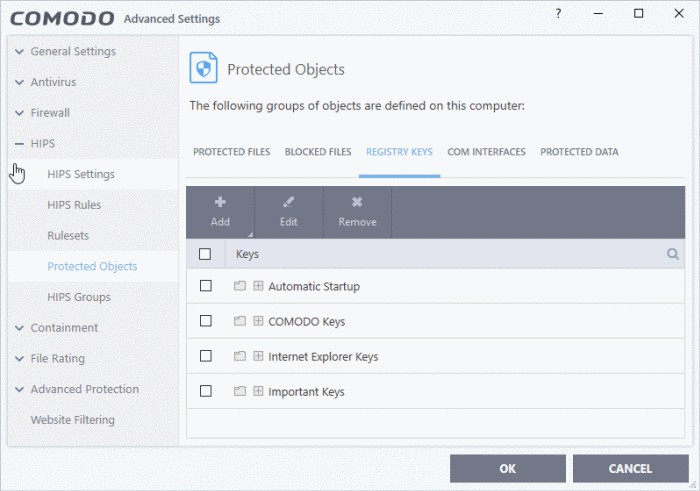
Aren’t these locations already protected here? If not, I guess that you can add them here manually:
Exactly! The same applies to this sample: 14 security vendors and no sandboxes flagged this file as malicious & Comodo did not detect it also - Comodo Forum
As they were, they are still protected.
The issue is whether the executable file is trusted in the cloud or unrecognized, if the file is unrecognized, depending on the rules, actions will be taken against this execution.
It might be that it’s listed as Trusted in the File List for some reason.
Yes. They are listed in the protected objects.
As I found RedStraw’s issues to be a bit concerning, along with the sample he provided I included 2 other similars as well as some other .js and.jar (with Java Runtime installed for the latter jar malware) confirmed malicious files. Also included was the file Tachion mentioned in Post 21.
I proceeded as follows: both on W10 and W11, for both the currently released version 12.2.2.8012 and the Beta Build 8088.
In each case the setup was:
Configuration- Proactive Security
Containment- Enabled at Default
Hips- Enabled at Safe Mode
File Rating- Disabled
VirusScope- Disabled
In all if the js and jar files that I ran would get this initial Containment Block (so nothing actually went into Containment as the thingies were precluded from activating
(the executable from Tachion Just went into Containment to die).
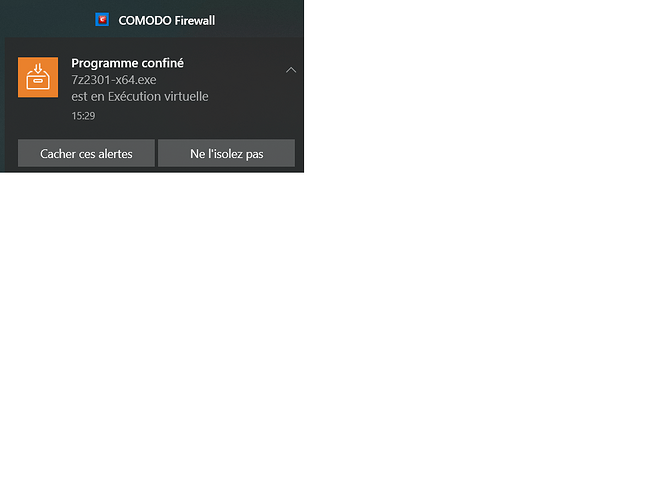
However, when I disabled Containment I did see the a couple HIPS popups like this
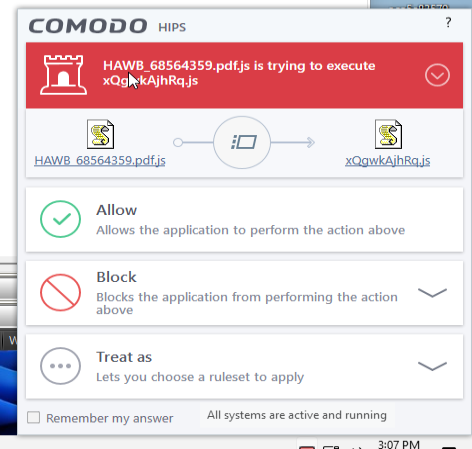
which is the prelude to Payload drop and AutoStart modification.
So, for whatever reason it seems that in RedStaws case Containment did not activate. For any that would like to test if Containment is working without screwing around with malware, the 22.01 build of 7=zip which can be found here should work:
https://www.7-zip.org/download.html
I normally would make some sort of video at this point, but sadly I went Roller-Skiing in preparation for the coming Ski Season and fractured my wrist (surgery this afternoon and they will die if a scar is left!).
@cruelsister Thank you for continuing to follow up on this issue and wishing you a speedy recovery.
Strangely, I don’t know what goes wrong with the CIS in my case. I have noticed that the latest antivirus database can detect it. If the containment won’t work in such situation, the detection can play a role. Many thanks again ![]()
W10 Famille - 22H2- 19045. 3324/ CFW : 12.2.2.8012
FW: safe mode, Auto-containement: enable, HIPS: safe mode, VirusScope: enable
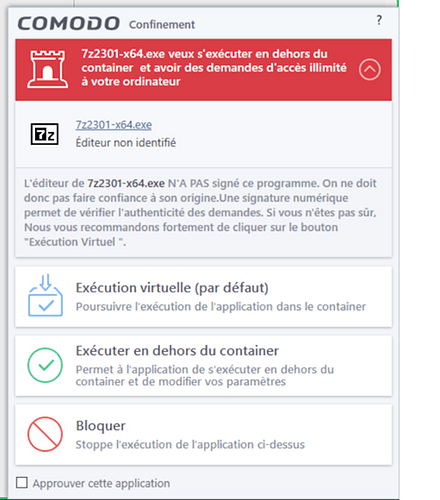
When I download the zip and want to open the file, this popup appears:
If I click on “Block” this message appears:
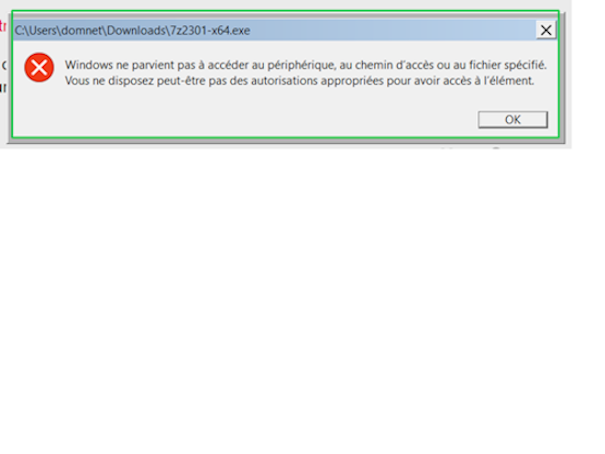
If I Choose “Run in the container” my administrator pwd is required to run the program.
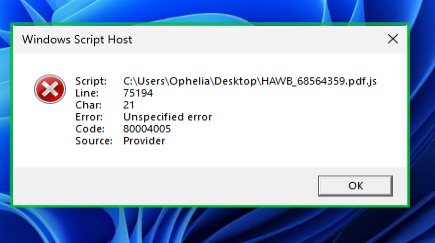
I didn’t get any notification and I noticed this message afterwards:
Cool-that’s exactly what should occur as the file, although totally legitimate, is not signed.Just wanted to verify that Containment on the system worked as a prelude for those not getting Containment for the J-Script malicious file previously discussed.
Strange situation. Opening a zip archive should not launch the 7-zip installer.