mouse1
February 7, 2014, 2:45pm
21
In Explorer +++ you need to
move Explorer+++.exe to a new folder
create an registry autorun entry for Explorer++ using Explorer ++ or a copy of regedit running from Explorer++in creating the autorun entry you must use the new folder as the path
This is working. I can make it do it myself!
Context
Move (not copy) self to autorun path
Move (not copy) self to other folder and copy link (shortcut) to self to autorun path
Move (not copy) self to other folder and set registry value in autorun key to self
Recognition operates only for unknown .exe files, not trusted or batch files
Most people don’t want to run malware to test VC.
One example might be a Windows explorer file manager substitute, though I would not recommend you use a full replacement Windows shell. But how do you arrange for it to be unknown? You could:
[ol]- find a relatively obscure one that happens to be unknown
find a beta version of a better known one which is unknown
remove the programs vendor and/or trusted file entry from CIS and disable all cloud interactions or disconnect your network connection
if the file’s license agreement allows this, over-write some irrelevant bytes in it’s executable file with a random string of equal length[/ol]
Please be careful when carrying out these experiments as user files created by detected unknown programs, or the programs they run, may be automatically deleted by reversals. So for example, based on my analysis of how VS is currently working, if you use your explorer or shell substitute to start an office program, create some files you want to keep, forget and then trigger a detection and don’t respond to the alert, the files will be deleted by the reverser. This is a bigger potential issue with a full Windows shell replacement, which is why I do not recommend using a substitute windows shell for this type of testing.Taking a full data backup before triggering detections is a wise precaution
There may of course be other ways. Please do report your experiences in testing using these techniques or any others you happen upon, below. Obviously please report bugs and wishes in the Beta bugs Board.
Best wishes
Mike
Can you please make a test on VIRUSCOPE
I began to doubt this feature effectively, because I tested a lot of viruses did not move, even for a one-time
ad18
February 8, 2014, 10:34pm
23
They have not added many recogizers (rules) yet. I don’t like it either but there is nothing to do but wait.
mouse1
February 9, 2014, 11:22am
24
Can you please make a test on VIRUSCOPE
I began to doubt this feature effectively, because I tested a lot of viruses did not move, even for a one-time
Hi Ahmad. I have tested extensively.
I don’t think you will get many detections from malware yet, as there are few recognizers.
Using explorer++ in the right way should get alerts. I have done so reliably using another explorer substitute.
But I think you have difficulty understanding how to do it. Google translate has limiations:)
If I get time I will post a video for you. That will allow me to try out Explorer++ as well.
Sanya if you are there, can you make VC trigger in Explorer++?
Best wishes
Mike
SanyaIV
February 9, 2014, 11:30am
25
I haven’t tried, simply because I don’t understand how to make a file move itself since that action wouldn’t be allowed because that file is already running… ??? I assume there is a way but I guess I’m just not good at replicating malware behavior. 88)
mouse1
February 9, 2014, 11:51am
26
Sanya IV Litvyak post:25:
I haven’t tried, simply because I don’t understand how to make a file move itself since that action wouldn’t be allowed because that file is already running… ??? I assume there is a way but I guess I’m just not good at replicating malware behavior. 88)
Actually in admin mode you can just do it
Hi Ahmad. I have tested extensively.
I don’t think you will get many detections from malware yet, as there are few recognizers.
Using explorer++ in the right way should get alerts. I have done so reliably using another explorer substitute.
But I think you have difficulty understanding how to do it. Google translate has limiations:)
If I get time I will post a video for you. That will allow me to try out Explorer++ as well.
Sanya if you are there, can you make VC trigger in Explorer++?
Best wishes
Mike
Thank you very much
SanyaIV
February 9, 2014, 12:03pm
29
Hmm no I still don’t understand. :embarassed:
Through explorer++.exe I cut it and pasted it in C:\Users\Sanya\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup … perhaps that’s not the autorun path or I’m just moving it in the wrong way? ??? Video? ;D
mouse1
February 9, 2014, 12:47pm
30
Sanya IV Litvyak post:29:
Hmm no I still don’t understand. :embarassed:
Through explorer++.exe I cut it and pasted it in C:\Users\Sanya\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup … perhaps that’s not the autorun path or I’m just moving it in the wrong way? ??? Video? ;D
Was BB off? [edit: thanks for testing!]
I have used|: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup for testing
Also try a menu based move if ex++ has it.
SanyaIV
February 9, 2014, 12:55pm
31
Was BB off? [edit: thanks for testing!]
I have used|: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup for testing
Also try a menu based move if ex++ has it.
BB was off yes, explorer++ crashes in partially limited however I did try a right-click sandbox and still no pop-up from Viruscope. Will try that folder you said.
Edit:
mouse1
February 9, 2014, 2:39pm
32
I had HIPS off as well, and the other two BB settings - it works
It won’t work FV
Path was: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
If you use ignore once, you’ll have to restart explorer++ before it will redetect.
Here is a video
SanyaIV
February 9, 2014, 2:51pm
33
I had HIPS off as well, and the other two BB settings - it works
It won’t work FV
Path was: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
If you use ignore once, you’ll have to restart explorer++ before it will redetect.
Here is a video
I set CIS like that and did what you did and still no Viruscope pop-up? ???
Edit: Is it too late if the SHA1 of the file is matched with a file on the Comodo File Intelligence? That would mean they already have the file no?
mouse1
February 9, 2014, 2:54pm
34
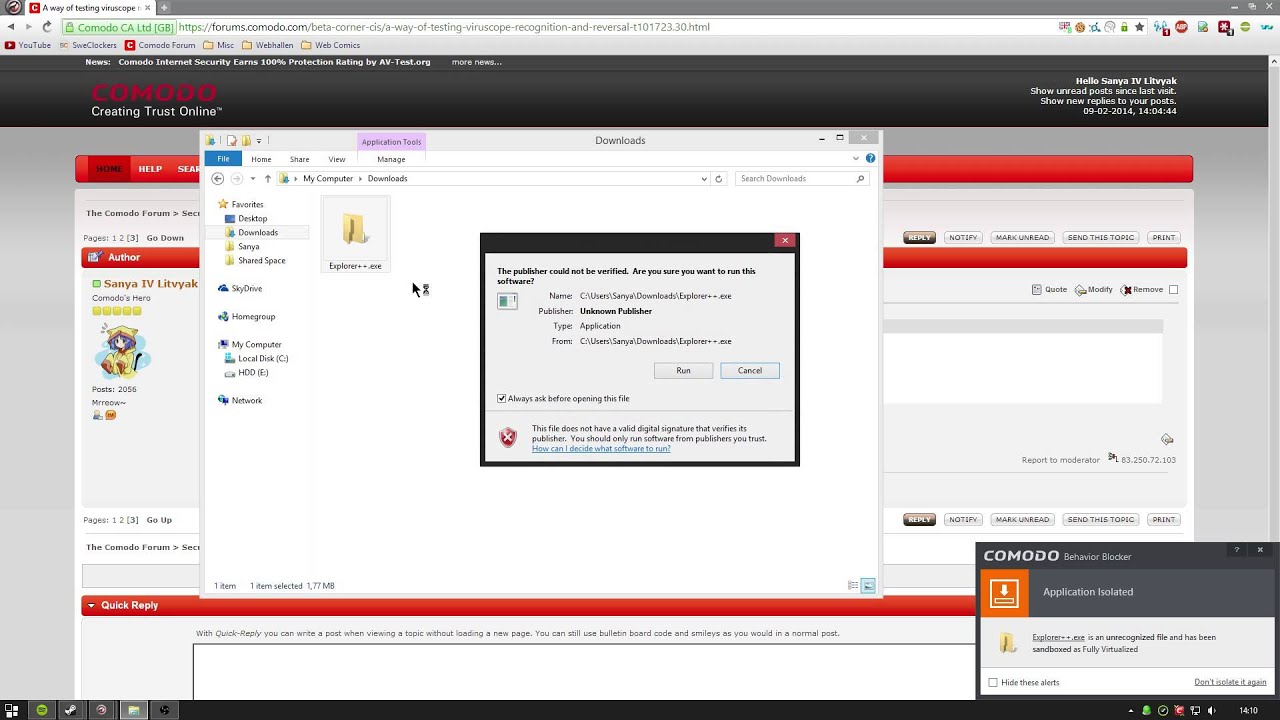
If you don’t like videos, steps are:
Check you have HIPS off, BB dis-abled and “detect programs…” and “show privilege…” also disabled (I don’t think HIPS off is needed but lets see!)
Check you have Cloud Lookup off
Run explorer+++
Run Killswitch and check explorer+++ is running as unknown
In explorer+++ navigate to explorer+++ directory and select explorer+++.exe
From menu choose Edit ~ MoveTo and in move directory selection dialog navigate to C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
Press OK, you should get VC alert
Choose ‘Ignore once’ if you want to repeat experiment and re-start explorer+++
SanyaIV
February 9, 2014, 2:58pm
35
Oh… fail… the recognizer .dll was missing from my computer… ??? (I’ve noticed that it gets downloaded now and then… does it delete itself or what?)
mouse1
February 9, 2014, 2:58pm
36
Sanya IV Litvyak post:33:
I set CIS like that and did what you did and still no Viruscope pop-up? ???
Edit: Is it too late if the SHA1 of the file is matched with a file on the Comodo File Intelligence? That would mean they already have the file no?
Hi Sanya. Try the text instructions - I can never follw videos myself
mouse1
February 9, 2014, 3:00pm
37
I’ll try to work that one out later. Maybe the update fail deletes it? I have not tried to update. Reinstall should fix…
SanyaIV
February 9, 2014, 3:17pm
38
So I updated the recognizer (since it wasn’t present on the system) and then I tried again but still no VC alert, I then reboot and tried again and now I get VC alert. So my thought is that updated recognizers don’t become active until system reboot… Just a theory.
Video of it working is available here: Testing Viruscope again. - YouTube
Sanya IV Litvyak post:38:
So I updated the recognizer (since it wasn’t present on the system) and then I tried again but still no VC alert, I then reboot and tried again and now I get VC alert. So my thought is that updated recognizers don’t become active until system reboot… Just a theory.
Video of it working is available here: https://www.youtube.com/watch?v=8vcHPr2A0ds
http://www.brooonzyah.net/vb/images/smilies/alp11.gif
finally
http://www.shmok3.net/vb/images/smilies/MonTaseR_176.gif