I cannot answer this now, I have no CIS on my PC. But HIPS must work under Sandbox, can you test a keylogger under Proactive mod?
Lets check the HIPS will alert or not under sandbox?
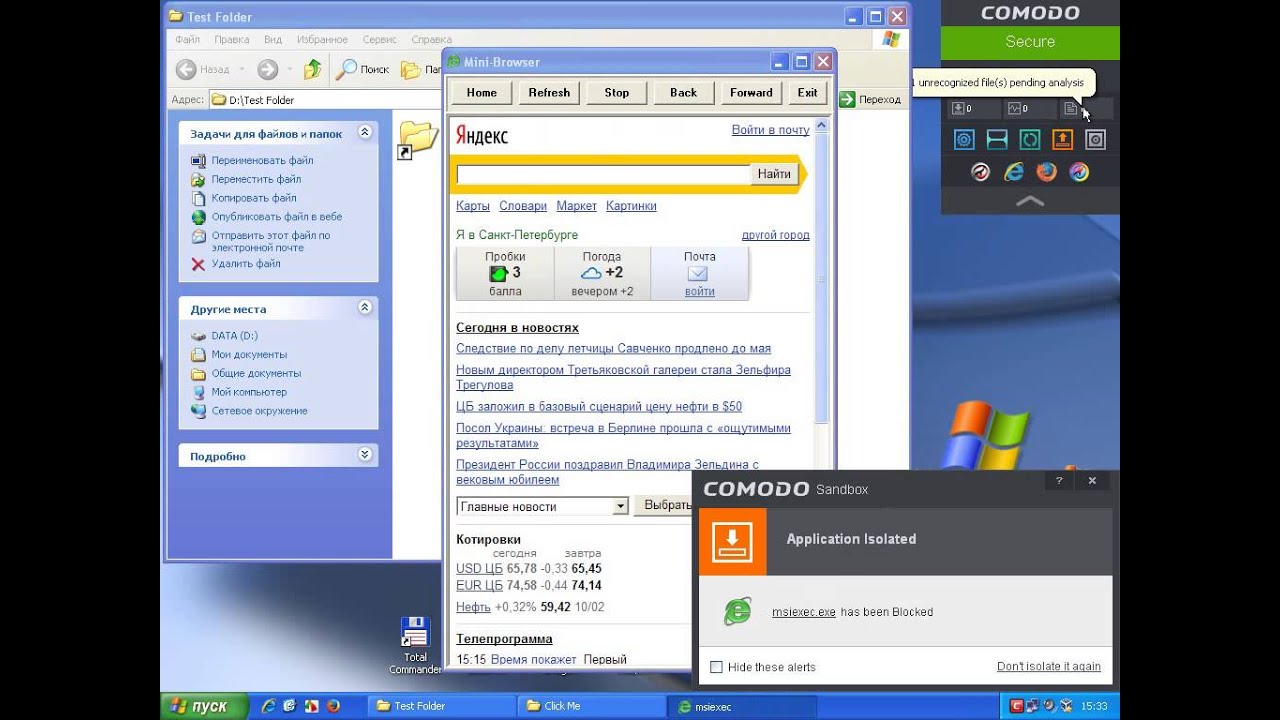
I tested this in advance in the video, and the result was blocked access to the keyboard
Then we need a wish for maus access block ![]() Will you create a wish for it?
Will you create a wish for it?
Great work Ahmad, I saw your latest video on this issue and the results showed a very grim scene. The RAT at the very least should of never been able to view the files never mind delete them. I’m pretty sure limited sandbox would of blocked this type of action but Comodo seemed to removed that feature in place of total virtualization. Do you think there are any settings that could be modified to prevent this kind of malware access or it is best just to deny the request to connect to the internet?
Comodo is not safe until developers fix critical bugs in Heur Cmd-Line Analysis. For example, video with curious situation is attached.
Nice view… >:-D
[attachment deleted by admin]
The problem is not monitored Contact malware , the problem is the engine Comodo a weak
For example: I can encrypt server Rat use a very simple encryption program and can not detect Comodo the server, I can not encryption server Rat on avira,eset
Because they need to have experience in programming, and also manipulated by Hex program to change the values, any hacker junior always find a challenge to encrypt server Rat on avira,eset
Because those programs have the protection of a powerful heuristics
Comodo also does not have a large white list, most programs are not digitally signed unknown, how to know if this is the application that is trying to connect to the Internet is malicious and how trust I will work with this software, Comodo needs to develop a white list and also Viruscope
Did you try the program Trend Micro Software He has the engine is very, very weak, but when you run the samples undiscovered You see that detects most of the samples by the advanced behavior blocker
In the video, even if Comodo block access to files, will be able to find many gaps
Even Sandbox limited partly also suffers from many gaps
The best way to address this malware Rat is Virtual Desktops and advanced behavior blocker"viruscope"
pleese see this video
It is good you are showcasing the weaknesses of Comodo. If the RAT is able to control the victim PC through the sandbox, then it isn’t much of a protection at all. Virtual desktop did protect the host PC from infection but the virtual sandbox should of done the same as well. I believe HIPS as well as firewall protection is still very valuable at preventing such a breach.
Keep up the good work SD Ahmad, your videos are very informative.
The test summary:
Partially limited: not prevent malware contact, I did not see any difference between enable partially limited or canceled enable,Comodo was unable to block access to the mouse
Limted:Also been contacted and control files victim,Comodo was unable to block access to the mouse
Restricted:the malware can not contact
untrasted: Was killed malware
Note 1: There are problems in the virtualbox program on the Windows 64 kernel for this I could not test the access to webcam “Not compatible fully with Usb”
Note 2:in CIS 7 Partially limited And above malware can not connect to the Internet
If you check this bug https://forums.comodo.com/, my answer is NO. Well, unless you tune the default Proactive Security configuration.
In my opinion, the auto-sandbox rules for unknown application could be improved.
If you decide to fully virtualize the app (default option), CIS fails some tests (for example, spyshelter tests - screenshot, keyboards and such).
If you decide to block the app (my previous choice), the app won’t start at all. But like this you don’t know whether it’s safe or not.
So, probably you may select “don’t block again” from the sandbox pop-up, but like this the app can run without any restriction (CIS will add it on the trusted files).
What I have personally done after checking the bug above is to keep the auto-sandbox enable, but with only the two rules to block any application rated as malware and any application targeting suspicious locations.
In this way, if the app is unknown, you will get a HIPS pop-up to alert you. Even if you allow the first of them, you’ll get other pop-ups when the app tries to do something else.
For example, you’ll get a pop-up when you click on spyshelter antitest.exe. If you allow it, you’ll get another pop-up when the app tries to start. If you allow it, you’ll get another pop-up when you try to perform a test (you’ll get a pop-up for every test).
Of course, if you allow this last pop-up, CIS will fail the test… but at least you’ll get several warnings and if you carefully read them, you can block it.
If you have any doubt on the app, you can block it first, then run it fully virtualized by right-clicking on the exe and choosing the option.
Maybe like this you’ll get many pop-ups, but I think it’s the best way to have a higher protection level.
Thx for that.
Well I don’t trust in this type of layer especially after I saw your test.
Can’t wait to see your next test :-TU
Hiya there
Is there by any chance a tutorial and/or video on how to configure CIS8 for good security ?
Thanks
Possibletarian
Hi Possibletarian,
The article in the link below is created by one of the Comodo Moderators.
https://www.techsupportalert.com/content/how-install-comodo-firewall.htm
Kind regards.
Thanks Captain, I will read that through ![]()
Possibletarian
I gave you my opinion about this case before.
Legacy antivirus products and their way of doing things is over. So those static heuristics mean not much if attacker wants to bypass them. Check out wikileaks and you will see how easy they are bypassed.
About viruscope, yes. Thats a technology which is behavior based and powerful. More recognizers are coming.
Is Viruscope will be able to detect worms and Bat malware , I tested many protection programs, but most of these programs are not able to detect Bat files or worms via blocker behavior
Unit Active Virus Control (AVC) Can not detect worms only by Signing Virus, And it applies to Trend Micro,System Watcher in kaspersky and eset
But why is it difficult to detect worms files Bat sometimes not be encrypted With these are not detected
BAT or script or any other file does not matter. If you share with file with me, i will see and let you know.
Are you serious? And what about these videos?
First video (from previous page) shows very curious situation, then Comodo “blocks” file, but it successfully runs and gets ‘trusted’ status and free Internet access. And even more: Comodo shows this file as trusted system file.
Second video (from there) shows more serious situation, then Winlock successfully run bypassing all layers of Comodo security.
No, it’s another case. File is running directly, not via Sandbox. Autosandbox settings - “block all”. Even more: with Autosandbox is OFF result is same.