The video description says the test was done using the latest CIS version of 12.0.0.6882 but in the video, you can see the virusscope recognizer is 12.0.0.6780, so it is kinda misleading. I have the sample used and I tested againts 12.0.0.6882, and I didn’t see any files get deleted like in the video and the how to decrypt your files txt document was not saved to the real desktop. So maybe the issue did affect 6870 but is now fixed in 6882, which might mean the sample used the vulnerabilities that were disclosed that affected 6870 to bypass the sandbox.
I ran the comment from the channel owner through an online translator:
ChineseRarypt does not encrypt the files as the typical ransomware does, instead, it places them in password-protected files, which users cannot access unless they pay the ransom fee demanded by the attackers, (the test was performed with the default setting of Comodo), I really thought that the Comodo sandbox would protect the files, I'm not sure what could have happened, maybe it could be due to a defect in the Comodo sandbox, one thing I could see was that only the files on the desktop were affected, (the same location where the ransomware was run), other locations such as the images / videos / documents folder, were not affected by the ransomware.Only the files on the desktop were affected.
I have several folders amongst which the desktop added to Protected Data Folders. That should have stopped the ransomware from deleting files on the desktop. It is unfortunate that Comodo does not add the default data folders of Windows to the Protect Data Folders by default.
default settins are useless
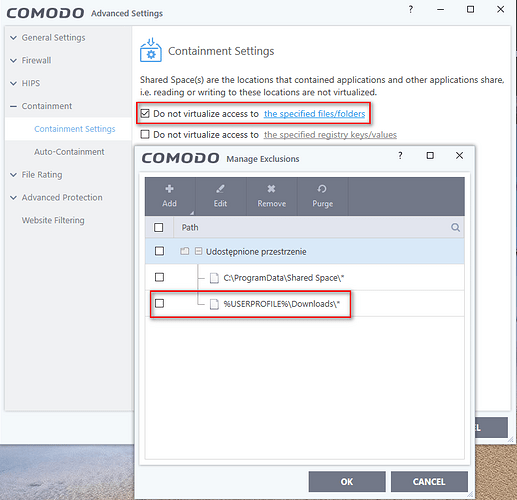
They have been removed from the downloads location, because it is the default location added in the program.
I watched the video and thought it was fake but no, now I can see that it is a bad CIS configuration… but then, @EricJH, by your explanation it bring me several doubts and questions:
1º You said that only the desktop folder is not protected by default again a sandboxed malware unless you add the the desktop to Protected Data Folders (Hips component). Then, by default the standard windows folders like Documents, Music, Pictures, etc… are protected by default again a sandboxed malware or you need to added to the Protected Data Folders?
2º Any other file/folders in others paths (same/other harddisk, usb memory, network path) are protected by default or not (I thought so)?.
3º The custom protection for the Protected Data Folders only works when the HIPS component is enabled or not?
Sorry if this isnt’s a place for help-questions but you answer brought me with many doubts…
This is why you use cruelsister settings.
I am using Proactive Security so I have HIPS enabled and I was arguing that my set up would have stopped this breech. For reasons of usability and ease of use I am strongly in favor of adding the standard Windows data folders to Protected Data by default or make a group that can be easily deployed.
2º Any other file/folders in others paths (same/other harddisk, usb memory, network path) are protected by default or not (I thought so)?.I will come to the analysis of this bypass further down. Sandboxed executables will only have access to the Shareed Space and Downloads folders as tachion is pointing out.
3º The custom protection for the Protected Data Folders only works when the HIPS component is enabled or not?That's what I assume but can't find it confirmed in the Help file.
Sorry if this isnt's a place for help-questions but you answer brought me with many doubts...To go further with the analysis of this bypass. Futuretech points out he is using 6870 and he cannot reproduced the findings of Juan Diaz. I have attached an image with the recognizers of 6882 to show that they differ. It indicates Juan Diaz was testing with 6870.
Futuretech could not reproduce the bypass and unless somebody shows otherwise this bypass does not affect 6882.
My Post have been deleted too, but I hope that have been an accident… ![]()
It is no clear what happen in this video, but one thing is true, is a bad video because we cannot see what happen when the sandbox is restored.
Anyway, it raised some doubts to me about the way that the sandbox works, so and going to create my own fake ransoware and test it with all CIS protection enabled to see what happen already with my files…
This is what he said (using the translator):
Yes, I tried to reset the sandbox but the files were not recovered, I also changed the configuration proactively and only got a notification from the HIPS module, maybe making other changes in the configuration could have protected the files, I don't know, I also believe the sandbox has some defect, I did a test with Sandboxie with this ransomware and it was able to protect all the files.
I have merged and removed duplicate posts from the CIS Certifications, Test Results & Reviews topic that discusses the video of CIS and the ChineseRarypt into this topic.
What ever version of CIS was used, it is clear it was not using default settings, I also tried with 6780 and I still didn’t see files on the desktop get deleted nor did I see the dropped text file get added either. So I have come to the conclusion that default settings were not used, in particular the ‘Do not virtualize access to the specified files/folders’ was modified to include the Desktop folder. So regardless of CIS version used, CIS will protect against this even under default settings.
I found it strange that only files located on the desktop were being modified and the ransom note was successfully being saved to the desktop, but all other files were protected. So it is either an intentional change to the do not virtualize containment setting, or an incompatibility with another security software that was installed alongside CIS during the test.
To answer the question of using protected data folders, HIPS does not need to be enabled for protected data folders to work. Also resetting the sandbox wouldn’t do anything to bring back files that were modified or deleted that were being excluded from virtualization.
Futuretech has split posts from CIS Certifications, Test Results & Reviews topic and merged them here. He also deleted double posts. May be double posts did get deleted.
Thanks for the analysis of this test in the video of Juan Diaz.
Obviously assuming that this is a true ransoware … so in conclusion, even not enabling HIPS protection and with CIS or CAV default settings, can you be calm?
Indeed. The bypass was not reproduced on both 6870 and 6882 by futuretech with default settings. There is no need to enable HIPS.
Great! Thank you! ![]() :-TU
:-TU
Good to know guys!
So, as I was suspected this video test is not clear/good and it seems that it has been done on unknown purpose…
@futuretech and @EricJH, Thank you for your tests and explanation!
So you tested with the sample from the video? Maybe this one?
Yes, also note that you need to have winrar installed specifically the 64-bit version of winrar if you are using a 64-bit Windows version.
Hey could you tell me where can I download the sample and run the test please?
It’s odd that this malware is presented as ransomware. Yes, it does drop ransomware notes in a few places, but otherwise it is a scriptor that deletes personal files (jpg’s, doc’s, etc). Recovery is quite easy using an search and undelete application like EaseUS.
A much more elegant ransomware that actually does plop files into password protected archive is something like https://www.virustotal.com/gui/file/c285e376201e2941154ec1a9acd8658cd5e0ea975c694a3fe3e9a9897efc2680/detection
Odd also is that a specific build of CIS would allow anything to be deleted as previous builds never did and the current application also protects. The initial malware file is sandboxed, as is the resultant spawn (rar.exe, taskkill, certultil, at, dllhost, etc.)
Finally it is a good idea to let the firewall show popups (unlike in the video) for stuff that should not be connecting out. certutil.exe attempting a connection to somewhere in China (Hangzhou?) is never a good thing.
I have HIPS enabled with the option to “do not show popup alerts” set to “block requests” no issues.